Top 5 Must-Know Phishing Simulation Templates - September Edition
We're back with a new installment of our monthly series featuring 5 Phishing Simulation Templates - brought to you by the Wizer Phishing team.
Phishing simulations are useful tools as part of your security awareness toolbox. Using a complete security awareness training and phishing simulation solution like Wizer's can give your program a boost in a stronger security mindset, strengthening your security culture.
Check out this month's featured templates to see what might be good to incorporate in your own in-person trainings or simulations. Look for the Download option at the end if you want to feature these in a training slide deck.
The online essential
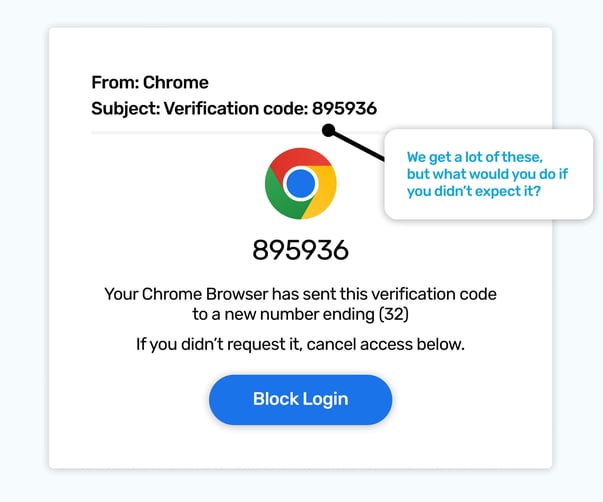
If you could only pick one app to have on a desert island, it would be hard to not choose a web browser, almost everything the internet offers can be accessed by them.
Over time, they get to know us well, and our most valuable personal data can be stored and typed into them. Which means compromising them is always on a scammer's wish list, as well as it being on their list of things we are more likely to want to keep secure, and updated.
The simulated phish above leverages the urgency we are likely to have to respond swiftly to any compromise of this important part of our digital world.
The recipient will know they’ve not requested it, so the first sentence will get them up to speed on why they have. And as this is a social engineering attack, it gets straight down to business! It clearly states it’s related to your Google Chrome browser, and that the verification code was sent to a new number.
The last few digits of a phone number shown are there to reinforce the fact part of your login process is going to a place you don’t know, and it’s natural at that point to want to stop it from happening.
The next sentence is the life-raft that perfectly seems to suit what you need right now! Yes! I do want to click and block the login.
This is a great example of how simulated phish can drill scenarios where your thoughts have already been craftily mapped out. During a busy day, we don’t have time to sit and think through every decision, a lot is done on autopilot. But by being aware of how the magic works, it helps us to better recognise when someone's trying to weave a hypnotic spell for us.
Color Curiosity
.jpg?width=603&height=503&name=Blog-Sept-teams%20(1).jpg)
Comment has been added; you’ve been tagged; access is requested… Our inboxes get a lot of notifications as we collaborate. Could you not respond to any of them? Well you could, but it would be like you had stopped turning up for work!
Scammers love things we can’t ignore, meaning collaboration notifications make useful simulated phish. This particular simulated phish doesn’t use fear, as a scammer might, but instead uses curiosity.
Would you be interested to see what the color was? And why were they less than impressed about being stuck with it? Maybe you wouldn’t… but these phish work because the curiosity can be satisfied instantly, with just a click.
These phishing templates and more available in Wizer Boost Phishing Simulation.
Catch and release
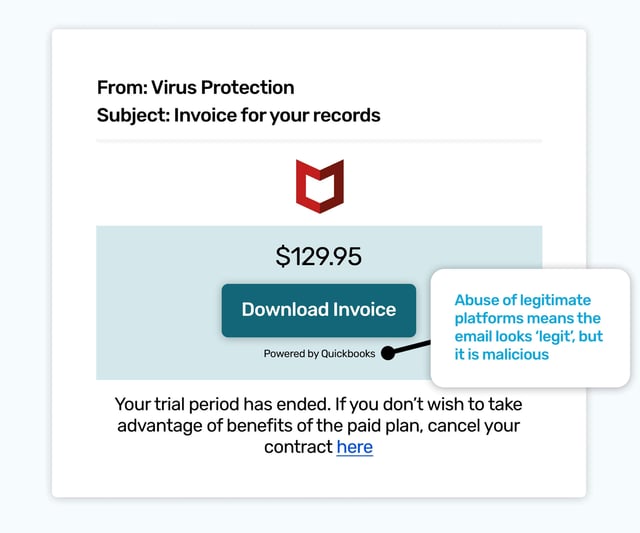
This simulated phish is based on one that’s seen ‘in the wild’. A growing number of phishing emails are using legitimate services; such as Google Forms, PayPal, and as seen here, Inuit Quickbooks, to add credibility to fake requests for payments.
It uses a virus protection organization’s identity, as these are exactly the kind of services we can accidentally activate a trial of, and forget we’ve done it - or even not realize we have!
Rushing to cancel subscriptions before we’re charged is an Olympic sport for some, and some services will even manage this part of your digital life for you.
As the recipient will not have signed up for a trial, they will be wanting to cancel it asap, and worry about how it came about after. Did a family member click something they shouldn’t have? Did I tick a box in the wrong place? All are technically possible… and that’s all they need to be.
The quickest route to rectifying this situation, as is so often the case, is to click.
Give me some space
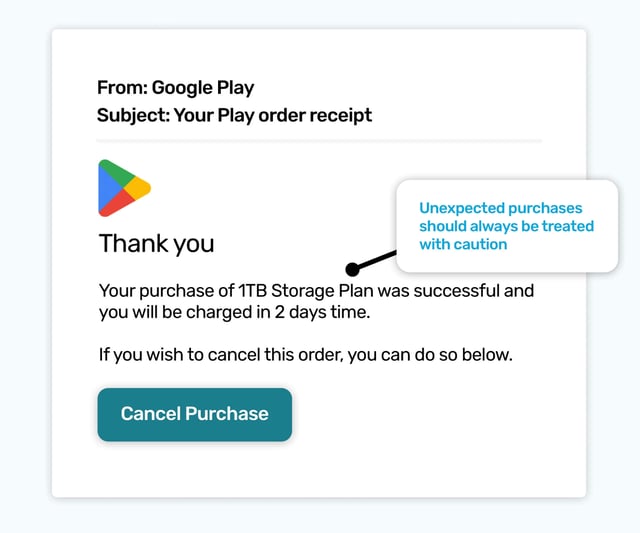
As Gmail is the most popular free webmail service, a simulated phishing email that related to an unexpected purchase of extra storage is a good way to illustrate that any paid additions to your Gmail account will fall under the heading of Google Play.
It would be a high value phish for a scammer, as canceling the purchase would require logging into your email account, and they could steal your login details.
If anything is becoming clear with this month's simulated phishing templates, it’s any unexpected renewal, or invoice, should be approached with caution. There’s at least as high a possibility it’s a phish than a problematic purchase that needs rectifying.
AI Invasion
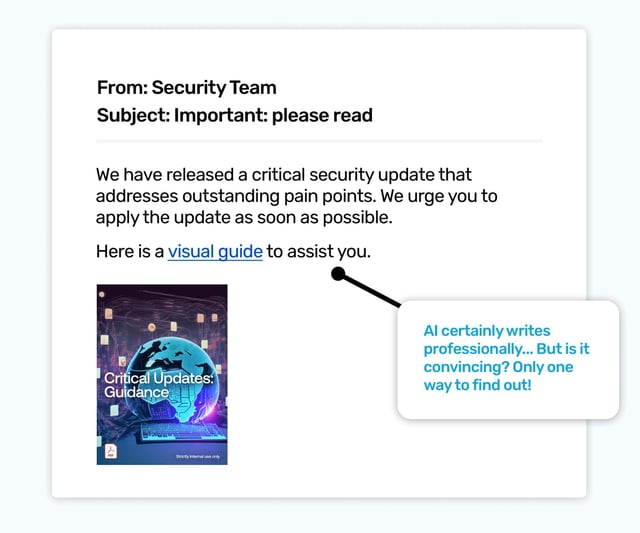
Now for something written by AI, intended for a Security/IT audience. Even the cover of the ‘guide’ was created by AI, so everything here was spun up by the pesky robots. Is it more convincing when it’s written by AI? Well, that’s one good reason to try a few simulated phishes that have been written by AI, you can gauge the risk they pose, and educate your colleagues.
Phishing simulations aren’t just about click rates, they’re also about using different types of phishing emails to learn something useful about your inbox ecosystem. That may be sending out a crypto phish to find out who would benefit from further education on keeping their wallets and NFTs safe, or, as we see here, finding out if AI generated phish are a new risk to take seriously.
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.
That's it for this month's phishing template ideas - looking for more ideas for phishing templates? Check out the resources below ⬇️ And check back next month for more!
Past Phishing Templates:
Top 5 Must-Know Phishing Simulation Templates - June Edition
Top 6 Must-Know Phishing Simulation Templates - May Edition
Top 5 Must-Know Phishing Simulation Templates - April Edition
Top 5 Must-Know Phishing Simulation Templates - March Edition
Top 5 Must-Know Phishing Simulation Templates - February Edition
- Pre-set Phishing Calendar for 2023
- Customizable Phishing Template Editor
- 100+ Phishing Templates
- Weekly Progress Reports