Top 5 Must-Know Phishing Simulation Templates - August Edition
We're back with a new installment of our monthly series featuring 5 Phishing Simulation Templates - brought to you by the Wizer Phishing team.
Phishing simulations are useful tools as part of your security awareness toolbox. Using a complete security awareness training and phishing simulation solution like Wizer's can give your program a boost in a stronger security mindset, strengthening your security culture.
Check out this month's featured templates to see what might be good to incorporate in your own in-person trainings or simulations. Look for the Download option at the end if you want to feature these in a training slide deck.
@ me attack!
Online life creates endless new things for us to adapt to; new apps, new processes, new problems, new colleagues, new redesigns, new requests, new sending addresses; it never stops.
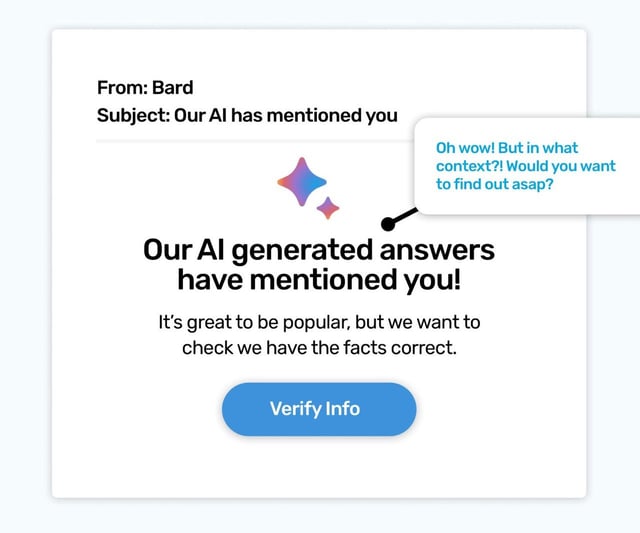
We don’t have a checklist of what exists and what doesn’t, and that does leave us open to being spun a tale that isn’t truthful. This simulated phish leverages a new Google product; Bard, it’s new AI assistant.
Google is so widely used around the world its new products will always be popular. And popular is a cyber criminal's best friend; each unknown inbox they land in they have a greater chance of resonating with the recipient - and that means more clicks.
By alerting someone to Bard’s answers having mentioned them, it’s pushing the curiosity buttons we all have; to want to know in what context we were mentioned; was it good, or even bad?! As with so many phish, to find out the answer you have to leave the safety of the email!
Phrases to phish
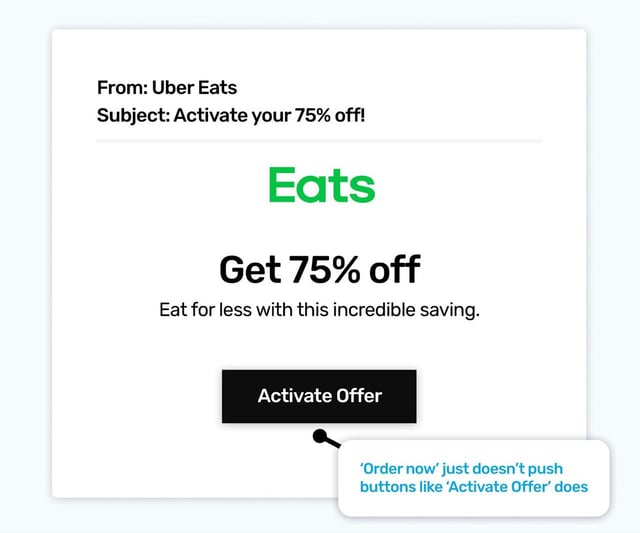
The humble button, or to use its formal name, the CTA (call to action), is a critical piece of the phisher's toolkit. It’s amazing how much work these can do to convert you into a clicker. The genuine email this was based on said ‘Order Now >’. Which makes sense when your goal is tempting people to order a cheap treat for dinner, but when it’s action right now you want, you need to get creative.
So the button now says ‘Activate Offer’, to tap into the ‘better to have and not need it’ mindset we all have when faced with something we might find valuable *at some point soon*. Sure, we could make a mental note, and come back when we’re feeling hungry. But what if the offer expires? At least if we activate it, we’re all set. And it seems like it’s just a click away.
Also, the original email said 40% off. Phish like to turn things up a notch! So if it seems too awesome to turn down, always be a little cautious, it really just might be too good to be true.
These phishing templates and more available in Wizer Boost Phishing Simulation.
QR (Quite Risky) Codes!
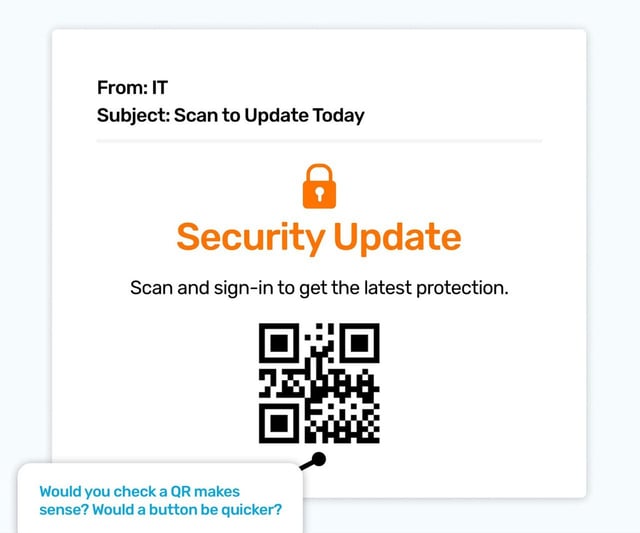
QR codes are popping up in phishing emails more often for a couple of reasons. Firstly it means a criminal doesn’t have to put a malicious URL in the body or code of the email; because security software can read them and then block the email. And a blocked phishing email is a useless phishing email!
Secondly, QR codes are not as tainted by bad experiences for most of us. We use them to select a pizza at a restaurant, or to show we have a travel pass; they haven’t got the bad rep the bright blue underlined link in an email can suffer from.
This is why QR codes within emails make good simulated phish, to safely illustrate that it’s better to be cautious when you get sent one unexpectedly.
And QR codes don’t always make sense in phishing emails. It’s good to question why a QR has been used if a traditional link might make more sense. QR codes help us pass over data quickly (like a flight boarding pass, or to link an account to a mobile app) and they also speed up access to a web page, when we might have not had our phone out (like accessing a menu, or the manual for a product we’ve just bought).
X marks the scam
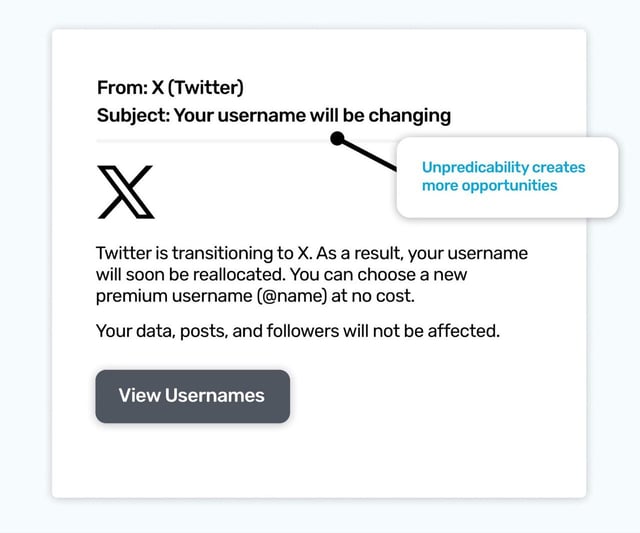
We’ve already mentioned how being online brings with it a need to always be learning about new things. And cyber criminals can weaponize our need to adapt and understand. What makes it more challenging is when unpredictability gets added into the mix, too. And perhaps the most visible moving target of unpredictability right now is Twitter, so we mean X.
Changes are happening so quickly and publicly it’s almost impossible to keep up, and the Twitter we may have known for so long has truly left the building. So our relationship and understanding about how they will act, and what they will say, is being entirely rewritten. And stories in the press about usernames being taken from people increase the uncertainty we have about X as a brand.
As cyber criminals thrive with unpredictability, it makes sense to drill these ‘chaos’ events safely with a simulated phish. You might think your username is not worth reclaiming… but can you really rule out it’s not been selected for ‘some’ reason? And even if you’re unsure, would curiosity make you want to see what premium names you’ve been offered?
Persuasive Proof
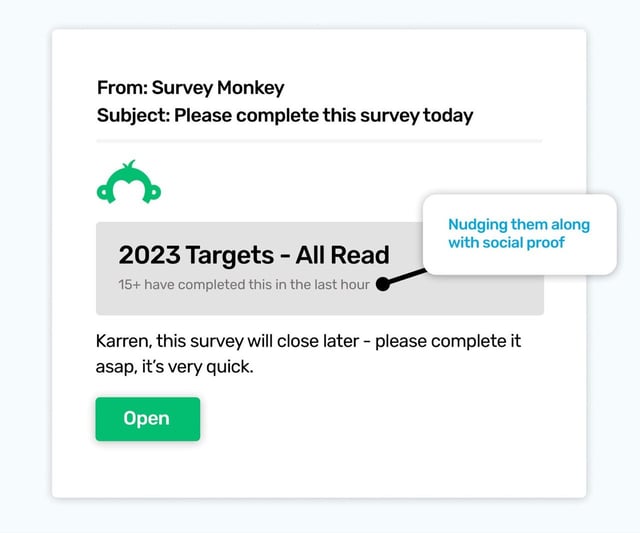
Survey Monkey can swing into any inbox and stand a chance of being trusted. Much like a Dropbox email, these solitary services might not be something you see often, but most businesses at some point will use a service other than Microsoft or Google to do a specific task.
The trust, or why we will respond to it, is usually based on what we take from the parts of the email we see as specific. In this example, the name of the survey starts telling the story; 2023 Targets - All Read. Okay, so it doesn’t not make sense, so far. Below that is a powerful little bit of social proof - it says 15+ have completed it in the last hour. And much like a retail website that says how many have just purchased an item, this can motivate us to act too.
The final personalized section mentions you by name, and doesn’t shy away from asking you to complete it today.
So for a simulated phish that has no more personalization than the average newsletter sent to 1000s, it tries hard to convince the recipient it’s legitimate.
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.
That's it for this month's phishing template ideas - looking for more ideas for phishing templates? Check out the resources below ⬇️ And check back next month for more!
Past Phishing Templates:
Top 5 Must-Know Phishing Simulation Templates - June Edition
Top 6 Must-Know Phishing Simulation Templates - May Edition
Top 5 Must-Know Phishing Simulation Templates - April Edition
Top 5 Must-Know Phishing Simulation Templates - March Edition
Top 5 Must-Know Phishing Simulation Templates - February Edition
- Pre-set Phishing Calendar for 2023
- Customizable Phishing Template Editor
- 100+ Phishing Templates
- Weekly Progress Reports


