Undermining Security Awareness
Security Awareness Training (SAT) educates employees about suspicious emails and the flags to look for - all very positive gains in the overall security posture of an organization. Yet, this training can be undermined by other departments or managers in the organization - or even by the security team themselves! How does this happen and how can we avoid it? Join us to learn from Amy Dearwester, Associate Director of Information Security Strategy & Innovation with a primary focus on the Security Champions initiative.
Amy Dearwester has sat in on her fair share of security awareness training in her days working in IT as just a 'regular' employee. Now that she's transitioned into cybersecurity - and brought her passion for people, technology, and training - her past not-so-pleasant experiences have given her a more critical eye. In this conversation, she kindly shares her insights gained to ensure the security awareness programs she implements also has a culture of security to support them so that the efforts for implementing effective training do not go in vain.
What does undermining awareness training look like?
Amy shared three real-life instances from her pre-security days to illustrate various ways the security awareness training she was given in past roles was undermined. Each instance focused on a different aspect of typical awareness training - phishing, business email compromise, and website security.
Phishing
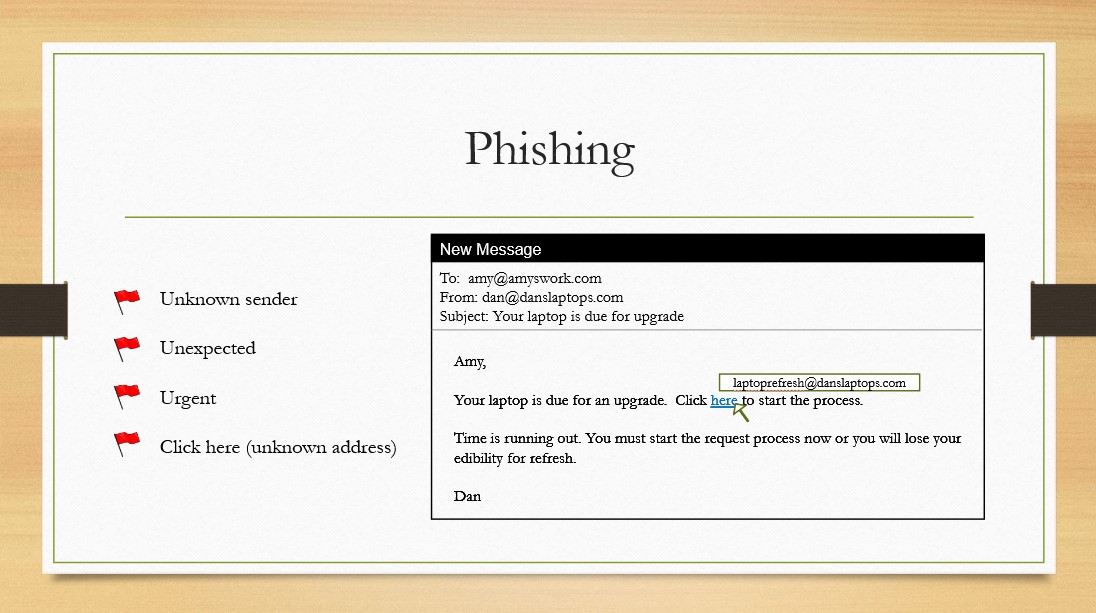
Her first phishing example dealt with an email she received at work that hit all the red flags she was taught to spot as attempted phishing. The email subject was regarding upgrades to her work device but it was 1) unexpected 2) came from outside her company domain 3) emphasized urgency 4) the call to action was a link to an unknown site.
Being a diligent employee, she reported the email only to learn that the message was indeed legitimate as the company had outsourced the upgrade. Worse, the security team poorly handled the report, making her not only feel bad but was told to 'just click it and complete the steps.
All of these missteps by the company would deter most employees from any future attempts to report or care about new emails that raise flags for them which naturally increases the risk of compromise and unravels any good previous training created.
Alternative ways this could have been handled to not undermine training include:
- Provide third-party vendors with a company email to communicate with employees
- Provide a URL to the third-party domain via the company intranet
- Receive the reporting positively and as feedback that there is a potential flaw in the way a particular messaging is being perceived
- Pre-empt the email with a company announcement notifying employees such an event is occurring
Business Email Compromise
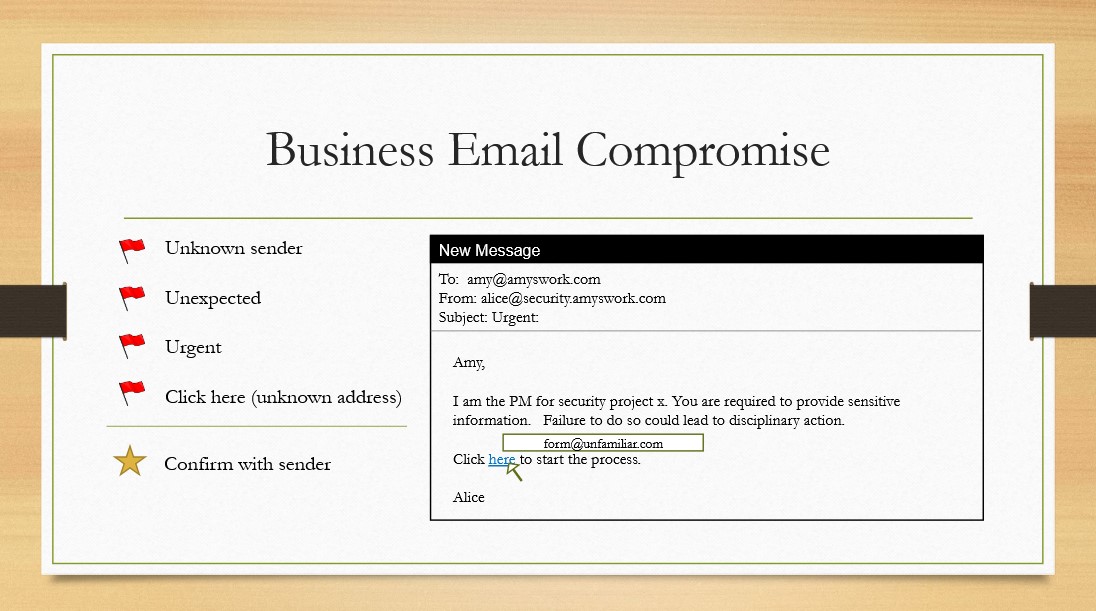
The next example dealt with an instance that strongly resembled a potential business email compromise attack.
Again, all the red flags were present as the email came from someone within the org whom Amy was not familiar with, on top of which was a member of the security team asking to provide sensitive information via a link to an unknown destination. Following the training she'd received in such circumstances, Amy reached out to the individual through a different channel of communication to verify the request.
Instead of being thanked for verifying, she received a curt response upset the email would be challenged and instructions to 'just get it done' - once again undermining any validity of past security training and increasing business risk in the future with employees encouraged to not question and to just click through.
Website Security
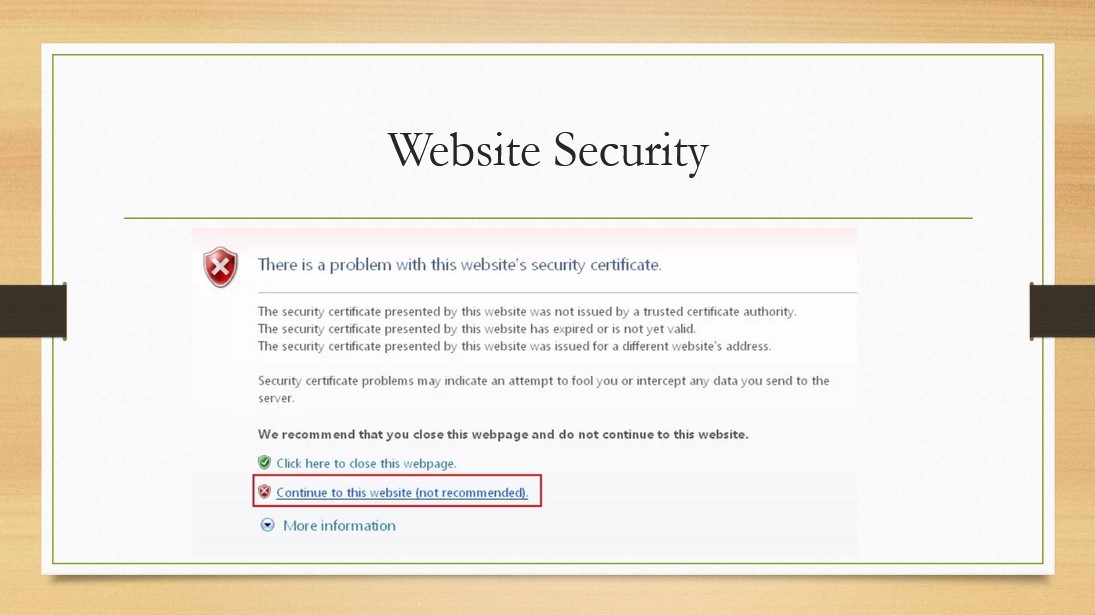
The final real-life scenario she shares starts off well - a company email notifying her an expected upgrade to her work phone is in progress and that she needs to visit a specific domain. All typical links check out and pass inspection so she proceeds to click. However, upon doing so she is met with a warning about the website's security certificate. Savvy from her past training that criminals can redirect legitimate websites.
One challenge in this instance was there was no direct line of communication with the security team to verify. As such, Amy turned to her manager to seek guidance as to the proper way to proceed and once again her efforts to verify legitimate concerns based on her awareness training were negated and put down.
Minimize the hot stove moments
For better or worse, it's a natural human tendency to remember negative or traumatic experiences more readily than positive ones. In short, we have a "negative bias". The common analogy of only touching a hot stove once can be applied to these same situations of negative encounters employees have in the context of security awareness which is something we really want to avoid as we work to build a strong security culture - the last thing we want is for them to shut down and stop implementing best practices!
We spend so much time discerning how to reach our employees with training that connects to them without considering where friction may be occurring outside of our workflow.
What Can Be Done To Prevent Undermining Security Awareness?
Positive Reinforcement - Automate follow-ups for reporting wherever possible but ensure a positive message is included. Consider crafting one message that simply thanks them for taking the time to report and craft a separate message that notifies the reported phish was actually spam and notate out a few reasons it was not a phishing moment. In other words, use these opportunities as positive teachable moments, even if they are automated.
Reporting - Make reporting as easy as possible for employees and even a rewarding experience, where possible. In the example of the website security certificate, if there existed a link internally for the employees to submit security concerns and for all those who reported instances that were verified to be legitimate, those names could be 'put in a hat', so to speak, for a monthly drawing or recognition.While it's been done for phishing it's another application of the idea.
Reimagine Training - Undermining security awareness training is not typically done intentionally, rather it happens in different instances where there exists a lack of coaching and procedures in place to minimize such occurrences. Automating workflows wherever possible can reduce negative messaging when the security team is under extra stress or having an 'off day'; and ensure management understands basic guidelines to create emails that don't raise all the red flags like a phishing email.
Granted some of these require collaboration across departments and getting leadership on board but the ROI in strengthening your company security culture.
Security Champions
Building a security champion, or security ambassador program, provides a two-way communication that can provide insights as to where potential 'holes' exist that may undermine the security culture. An ambassador program allows open dialogue between representatives across the organization and the security team which improves the ability to adjust your training to relevant scenarios. For a more in-depth discussion on how to build an ambassador program, check out our conversation with Nandita Bery.
Amy suggested a few other ways to get insights into your security culture through coffee dates for a casual conversation with individuals across the company to mentoring to more out-of-the-box approaches to gauge culture.
"Culture trumps your training any day of the week so you have to be aware of what your security culture is in your business."
Amy's Take Aways:
1 - Be aware the culture trumps training.
2 - Get out of your comfort zone to discover where the culture needs improvment.
3 - Collaborate with others within the organization to 1) make it easier for employees to 'do the right thing' and 2) create positive reinforcement of good behaviors.
Connect with Amy Dearwester on LinkedIn and while you're there check out our Security Awareness Manager community.
Other Resources:
Building a Winning Security Awareness Program - Interview with Dennis Legori
Creating an Ambassador Program for Security Awareness Programs - Interview with Nandita Bery
Building Healthy Security Cultures - Interview with Nadja el Fertasi
- Free Security Awareness Videos
- Quizzes
- Progress Reports and Certificates

Ayelet HaShachar Penrod
A passionate security awareness advocate, I connect and support security professionals as a Community Manager while also managing customer accounts for **Wizer Managed**, our security awareness service. Driven by 4 years of learning from cybersecurity experts, I’m committed to making security awareness accessible to all—individuals, small businesses, nonprofits, and enterprises alike.


