What Every Developer MUST Know About PCI DSS 4.0
In an age where digital transactions reign supreme, protecting sensitive data is the linchpin of trust between businesses and their clientele. Enter the Payment Card Industry Data Security Standard (PCI DSS) 4.0, the latest beacon guiding developers in their quest to fortify applications against potential threats.
This short blog serves as a deciphering manual, breaking down the enigmatic language of PCI DSS 4.0 requirements into plain English. From thinking like a hacker to patching vulnerabilities, join us on this journey as we unravel the intricacies of PCI DSS 4.0 for developers. Check out our Quick Reference PDF at the end.
PCI DSS 4.0 Requirement 6.2.1
It basically means that your dev team really needs to focus on how they're going to keep PCI Data, like credit card info, safe within the app.
It's all about thinking like a hacker. They've got to figure out how someone might try to crack the code and then build defenses against that.
This means nailing down the basics, like getting authentication and authorization spot on, encrypting the PCI data properly, and making sure none of that sensitive info slips into debug logs.
Now, this isn't just a last-minute thing. They've got to bake this security mindset in right from the start, from the design phase way before they even start coding, and keep it up all the way through to when the app goes live. One way to help your team with this is providing them with secure code training that meets PCI DSS 4.0 requirements.
PCI DSS 4.0 Requirement 6.2.2
This one is simple – developers need to learn how to write secure code, which means they need to be trained at least once a year.
But here's the thing, developers think like builders, they're all about, well, building apps. However, they don’t think like breakers. They're not used to breaking into apps or considering how others might try to do so.
So, even if your devs are top-tier, it doesn't mean they're wired to think like a hacker. They need to learn how to secure their code, understand the hacker mindset, and get familiar with the tools out there that can detect vulnerabilities in their code and put their fixes to the test. Luckily, Wizer Training has an amazing solution for secure code training to help you out. :)
PCI DSS 4.0 Requirement 6.2.3
Before you roll out your app or a new update, someone needs to review the code, making sure it's secure. Who's gonna do the review? Definitely not the person who wrote it – nope! You need either another pro who's skilled at spotting security flaws or use automated tools, like scanners that are designed to scan for vulnerabilities in the code.
This is an iterative process - if issues were found they need to be fixed and reviewed all over again.
PCI DSS 4.0 Requirement 6.2.4
This requirement specifies the types of attacks to provide clear guidance, moving beyond a mere "to the best of my knowledge" approach. All these types of attacks and how to defend against them should be explained during the developers' secure code training. Additionally, as outlined in Requirement 6.3.1, your code should be reviewed for these types of vulnerabilities before launching your app or releasing a new update.
PCI DSS 4.0 Requirement 6.3.1
Not all vulnerabilities are created equal. Some are high-risk, others low-risk, and it's important to label them accordingly, or at least identify the high-risk ones.
You also need a process to handle them effectively. This includes documentation, assigning responsibility, prioritizing tasks and making sure that bugs are fixed. If you discover a high-severity vulnerability affecting customer data, you may even need to activate your incident response team to check for exploitation. Additionally, your dev team should stay informed about vulnerabilities in any third-party libraries or products they use to ensure timely patching.
Help Your Dev Team #CodeWizer With Wizer For Developers
Specialized Secure Code Training
PCI DSS 4.0 Requirement 6.3.2
PCI DSS 4.0 Requirement 6.3.3
This requirement focuses on patching third-party libraries/software used by your dev team. In Requirement 6.3.1, we discussed labeling vulnerabilities by risk. Having done that, you should prioritize patching any high-severity vulnerabilities within a month and address lower-severity ones later, for example, within three months.
PCI DSS 4.0 Requirement 6.4.1
If your application is a web-based solution, such as a website or Software-as-a-Service (SaaS), it is more prone to attacks because it is open to the public. Therefore, you need to conduct a thorough check at least once a year or every time you have a major release. You should either find a professional in application security to do this or use automated tools that are designed for the task.
Regardless of the method you choose, you need to test for the requirements listed in Requirement 6.2.4, and if you find any vulnerabilities, they should be fixed based on the priorities listed in Requirement 6.3.1.
Another option you might consider is a solution like a Web Application Firewall that was designed to constantly monitor the traffic and detect attack attempts on your web app. You can set it up to either block potential threats outright or send alerts so someone can jump in and investigate immediately. Just keep in mind that whatever solution you are using it needs to be able to detect the types of attacks listed in requirement 6.2.4
PCI DSS 4.0 Requirement 6.4.2
This is very similar to the previous requirement 6.4.1 and will replace it eventually. It focuses on automatic tools like Web Application Firewall. You need to ensure that it is configured correctly, always up-to-date, and that someone is constantly reviewing the logs. Additionally, whenever there is an alert, it should be investigated immediately.
PCI DSS 4.0 Requirement 6.4.3
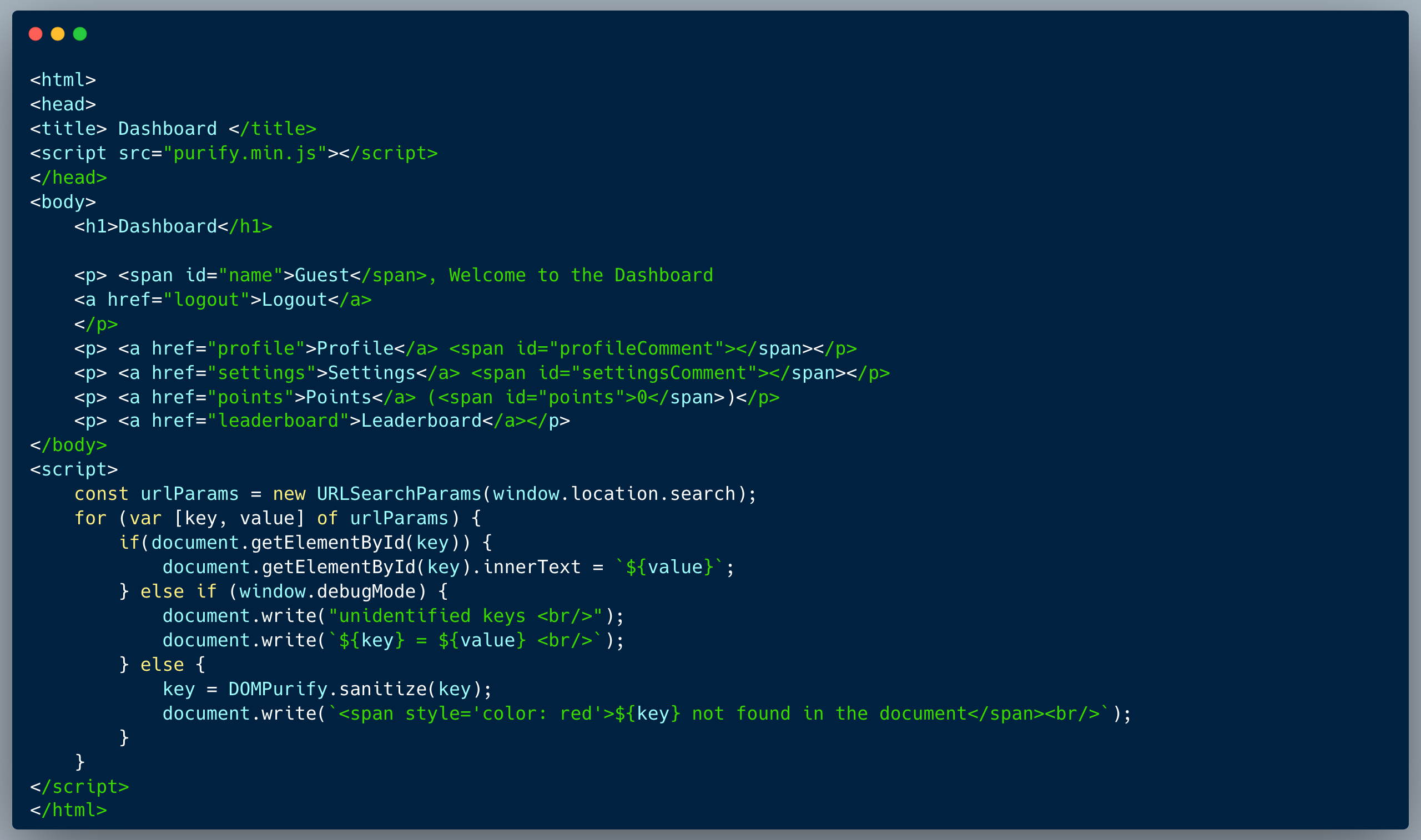
If your website has payment pages, such as a checkout page, cart, etc., you need to ensure that an attacker cannot manipulate these pages by including a malicious script. If the hackers succeed, they could capture the credit card information entered by the user and steal it.
This concept is similar to the need for protecting physical devices used for swiping cards. There are various ways to safeguard these pages - such as using a Content Security Policy (CSP) - to ensure that scripts can only be loaded from authorized locations. Part of the secure code training required involves teaching developers how to implement these protections.
.png?width=389&height=973&name=PCI%20DSS%204.0%20For%20Developers%20IG(1).png) Download Our PCI DSS 4.0 Quick Reference PDF
Download Our PCI DSS 4.0 Quick Reference PDF
Secure Code Training
As the digital landscape evolves, so must our defenses against potential threats. PCI DSS 4.0 Requirement 6.2.1 to 6.4.1 places developers at the forefront of this security paradigm shift.
From cultivating a hacker mindset to meticulous code reviews, each requirement serves as a layer of armor in the battle against cyber vulnerabilities. Developers are not just coders; they are architects of secure digital ecosystems.
Need help getting your dev team up to speed on secure coding as well as helping them learn to think like a hacker to build defensively? Check our newest offering Wizer for Developers.
CODE WIZER!
- From Owasp 10 To Advanced Techniques
- Deep-Dive 1 new topic monthly
-
Fun CTF Challenges to apply learning


Gabriel Friedlander
Gabriel Friedlander is the Founder & CEO of Wizer, whose mission is to make basic security awareness a basic life skill for everyone. Wizer has been rapidly growing since being founded in 2019, and now serves 20K+ organizations across 50 countries. Before founding Wizer, Gabriel was the co-founder of ObserveIT (acquired by Proofpoint). With over a decade of experience studying human behavior, he is a prolific content creator on social media, focusing on online safety to elevate public understanding of digital risks. His engaging 1-minute videos have captured the attention of millions worldwide, going viral for their impactful messages.