New Security Awareness Content for Spring
Spring has sprung and along with it comes all new CyberSecurity Awareness videos, webinars, life lessons, and even a little something for the DEV team. Plenty of exciting and relatable content to keep you and your teams engaged!
OWASP TOP 10 TRAINING (FOR DEV)
10 videos, each one minute long and to the point. Let's start securing data from the first line of code. Get your developers trained today! Oh yeah...and they don't even have to sign up because it's FREE!
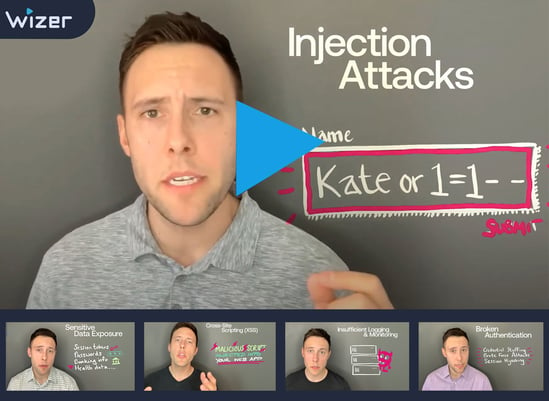
Injection Attacks
Injection attacks are when malicious code is fed into the user interface to try and trick the interpreter into carrying out unintentional commands like accessing data without permission. Learn ways to protect your code against these attacks.
Watch All 10 OWASP Videos Here!
- Register and log in to Wizer (great for tracking progress) OR
- View them all right off our OWASP TOP 10 Web Page - No Sign Up Needed!
Security Awareness training
The Dangers of Plugins
It seems simple. You're working with an app and need to do one little thing but you need a plugin and there it is readily available and easy to install. But, is it worth it? What are the risks?
More Videos to Watch and Share
Secure Communication
Think about the type of information you are sending when replying to emails, texts, and other messages. In addition, think about the method you are using to send the information. For example, sending a social security number via text is probably not the greatest idea. Learn best practices by watching Secure Communication below.
More Videos to Watch and Share
Brand new webinars (on demand)
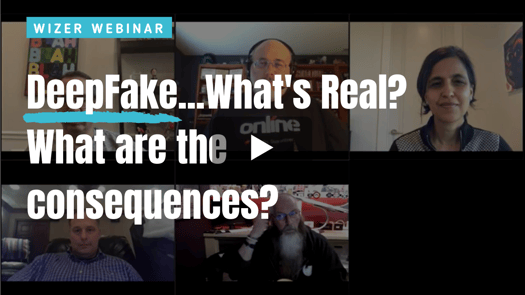
DeepFake...What's Real and What are the Consequences?
Apps that are meant to be fun could actually have adverse reactions in real life. Technology is advancing faster than we can keep up with and we are seeing more DeepFake videos and photos than ever. What kind of an impact could this have on society?
What is Zero Trust?
"You can't spin ZERO TRUST as identity, it doesn’t work like that... Zero Trust is a strategy decoupled from the technology. It isn’t a product, you need to look at it strategically," said John Kindervag who created the term Zero Trust. Listen to John and our other esteemed panelists in this eye opening webinar.
View the Entire OnDemand Webinar Library
Real Life Lessons
How My Kid's Instagram Account Got Hacked
Imagine your 12 year old kid gets a DM from her friend that she is in the TOP 10 UGLY list in school! Ouch… This is a TRUE STORY about how almost everyone in her grade got hacked.
I Really Thought He Was In Jail
Many of us have heard story after story about an aging family member or older colleague that has been taken advantage of by cybercriminals. Watch the true story unfold on how exactly this happens.
How Our Co-Worker Hacked The Company
We're talking about a true Insider Threat story in this next video! Yes, even a coworker can hack a company. Find out what happened.
You are 30 seconds away from having a Security Awareness Program.

Gabriel Friedlander
Gabriel Friedlander is the Founder & CEO of Wizer, whose mission is to make basic security awareness a basic life skill for everyone. Wizer has been rapidly growing since being founded in 2019, and now serves 20K+ organizations across 50 countries. Before founding Wizer, Gabriel was the co-founder of ObserveIT (acquired by Proofpoint). With over a decade of experience studying human behavior, he is a prolific content creator on social media, focusing on online safety to elevate public understanding of digital risks. His engaging 1-minute videos have captured the attention of millions worldwide, going viral for their impactful messages.
white%20arrow.png?width=525&name=Zero%20Trust%20Thumbnail%20(2)white%20arrow.png)



