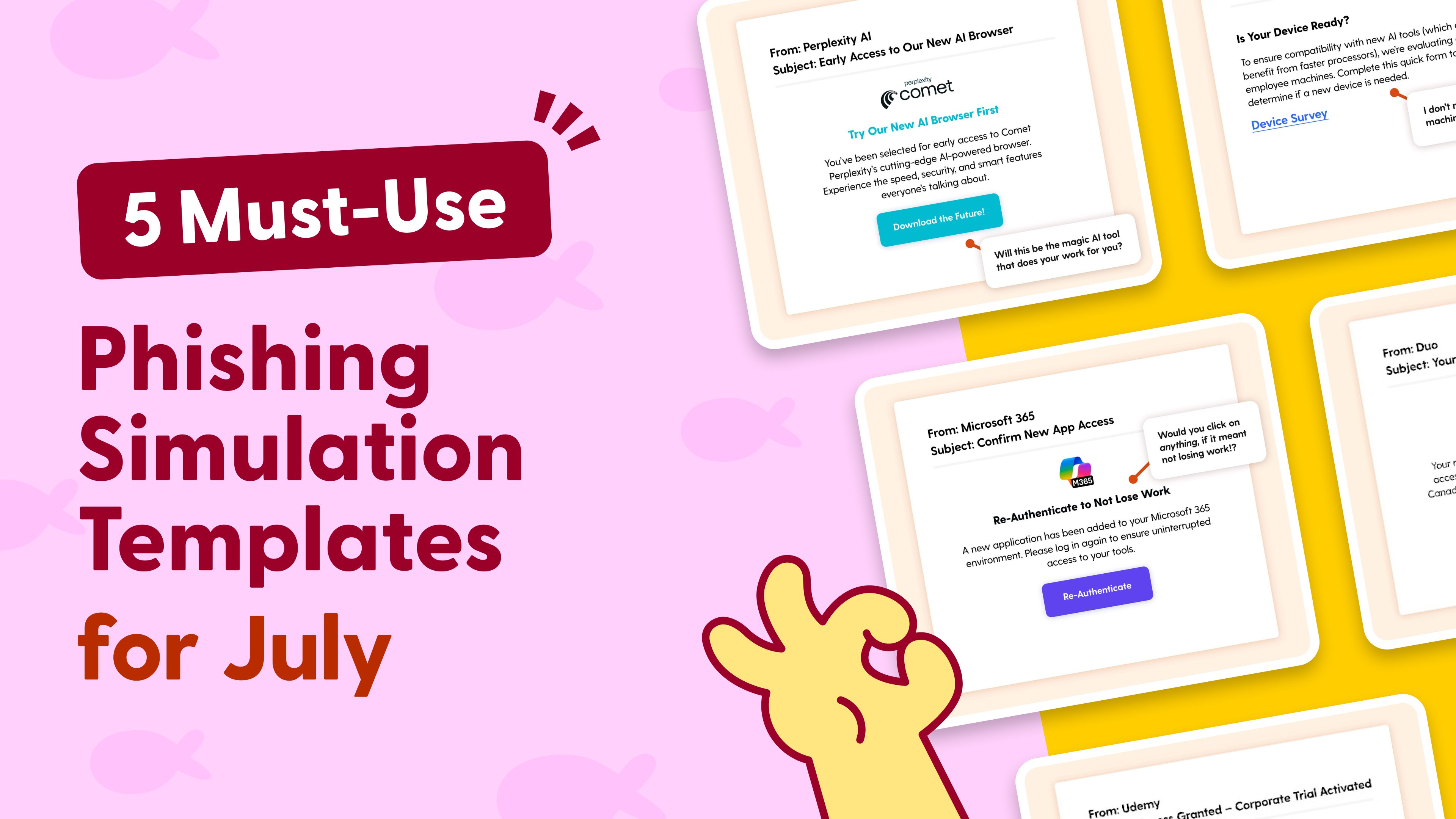
5 Phishing Simulations to Master This November
November starts holiday shopping frenzy but it's also when organizations hit Q4 stride—budget approvals, year-end planning, and performance tracking intensify. Attackers exploit this momentum, using urgency and familiarity to slip past defenses. These five simulations reflect current tactics targeting routine workflows and emerging tools.
Here are five new phishing simulation templates to incorporate into your training program this November.
Download these phishing templates for your in-person security awareness training materials!
Calendar Chaos

Scenario: Employees receive an email from "Google Calendar" or "Outlook" warning that multiple calendar events were automatically deleted due to a sync error. A "Restore Deleted Events" link is provided.
The Hook: Calendar integrity is critical for professionals. The fear of missing meetings or losing important appointments creates instant panic. The technical explanation ("sync error") sounds plausible enough to bypass skepticism, especially for users who've experienced legitimate sync issues before. Would you risk missing important meetings, or click to check what's gone?
Real-World Risk: Clicking leads to a credential-harvesting page that mimics your calendar service. Since calendar access often includes meeting details, attendee information, and organizational insights, compromised calendars provide attackers with reconnaissance data for targeted attacks.
Tips for spotting this phish:
- Calendar services rarely email about sync errors—they show in-app warnings
- Check your actual calendar directly before clicking any links
- Look for vague details (which events? when were they deleted?
Office Updates
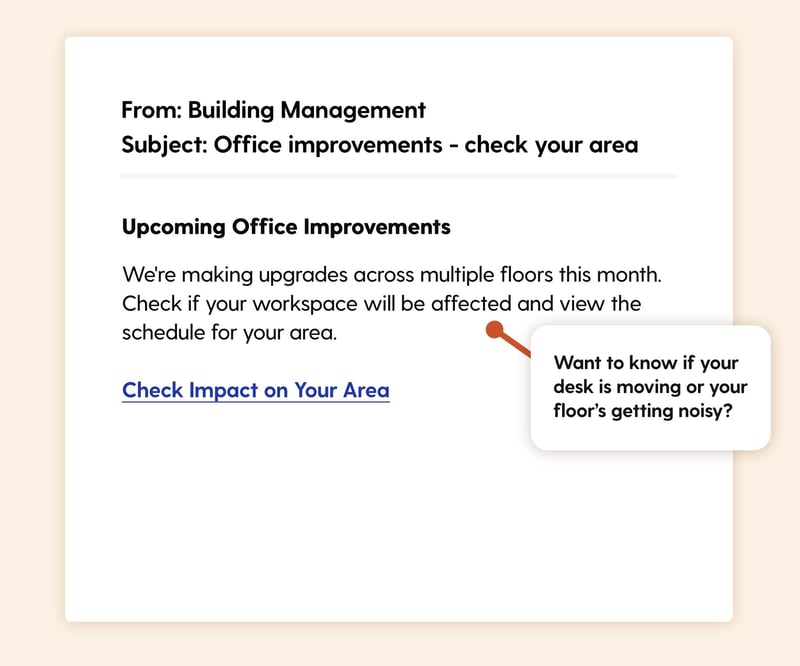
Scenario: An email from "Facilities" or "Building Management" announces upcoming office improvements and renovations. Employees are asked to "Check if your workspace will be affected" by clicking a link to view the schedule for their area.
The Hook: Office changes affect everyone—desk moves, noise, access disruptions. Pure curiosity driver: "Will this affect me?" Combined with practical need-to-know for planning purposes. Wouldn't you want to know if your desk is being moved or your floor will be noisy?
Real-World Risk: The link mimics an internal facilities portal to harvest credentials, or leads to a malicious site requesting "verification" of employee details for "workspace planning."
Tips for spotting this phish:
- Legitimate office updates typically come through established internal channels
- Check with facilities directly or look for announcements on your company intranet
- Be wary of urgent requests for personal information related to facilities planning
Company Perks Platform
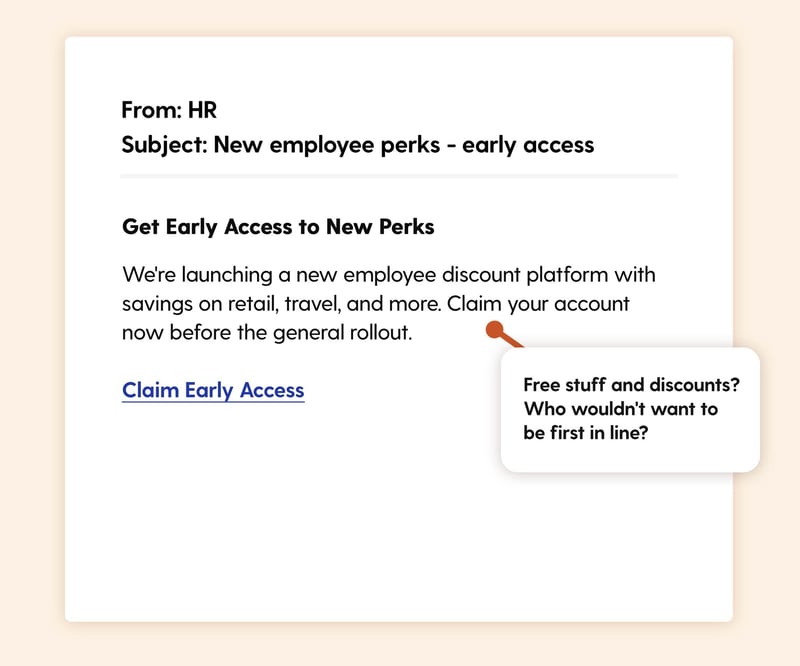
Scenario: HR announces a new employee discount platform with savings on retail, travel, gym memberships, and more. The email offers "early access for staff" and encourages employees to "claim your account before general rollout."
The Hook: It's a positive thing—new benefit, not a problem to fix. "Early access" creates mild FOMO without pressure. Employee discount platforms are common enough to be believable but not so routine that people know exactly how rollout works. Free stuff and discounts? Who wouldn't want to be first in line?
Real-World Risk: The fake platform signup page harvests credentials or personal information under the guise of "account creation." Attackers can use this data to access other corporate systems or sell employee information.
Tips for spotting this phish:
- Verify new benefit programs through your HR department directly
- Check if the sender's email domain matches your organization's official HR communications
- Be cautious of "early access" offers that require immediate action
Canva Collaboration
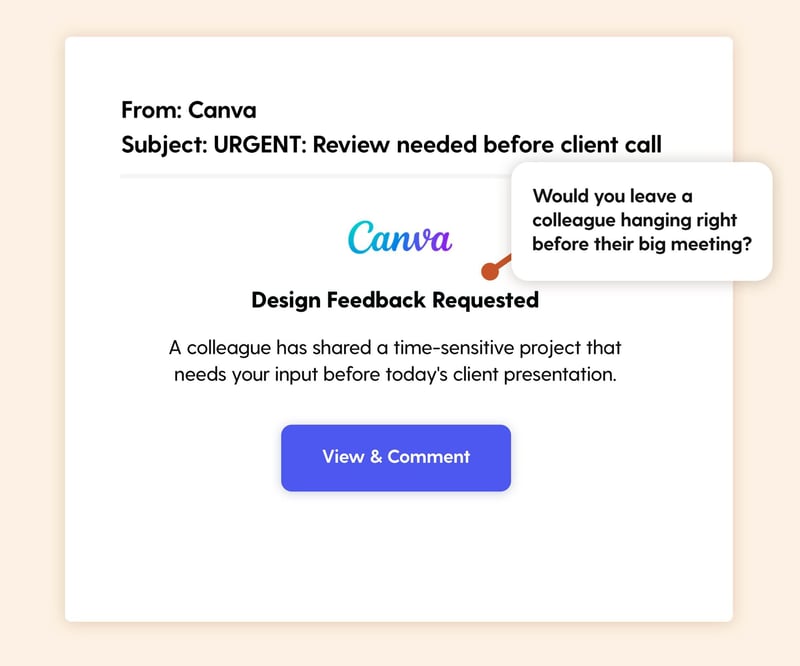
Scenario: Email states that a colleague has shared a time-sensitive design project on Canva that needs immediate feedback. Subject line: "URGENT: Review needed before client call."
The Hook: Collaboration tools create legitimate urgency—real work depends on timely feedback. Canva's popularity across marketing, HR, and operations makes this broadly relevant. The "client call" deadline adds business pressure. Would you leave a colleague hanging right before their big meeting?
Real-World Risk: The link directs to a fake Canva login that steals credentials. Since many organizations now use Canva for business with SSO integration, compromised accounts can provide attackers with access to broader corporate systems, brand assets, and client information.
Tips for spotting this phish:
- Hover over links to verify they lead to canva.com
- Check if you actually use Canva or have an account
- Verify with the supposed sender through another channel
GitHub Security Alert
Scenario: Email appears from "GitHub Security," warning that a critical vulnerability has been detected in one of your repositories. Requires immediate review and patch. Includes "View Security Advisory" button.
The Hook: For technical teams, security vulnerabilities demand immediate attention—unpatched repos can expose entire codebases. The official-looking format and security jargon (CVE numbers, severity ratings) add legitimacy. Developers are conditioned to respond quickly to security alerts. Could you ignore a security breach in code you're responsible for?
Real-World Risk: Clicking leads to a fake GitHub login page. Compromised developer accounts provide access to source code, deployment keys, and potentially production systems. For organizations, this can mean intellectual property theft or supply chain attacks.
Tips for spotting this phish:
- GitHub alerts appear first in the Security tab of affected repositories
- Check the sender address carefully (github.com, not github-security.com)
- Verify through your actual GitHub dashboard before clicking email links
- Real security advisories include specific CVE numbers and repository names
The Human Layer: Your Strongest Defense
These simulations exploit specific conditions: Q4 pressure makes deadline-driven requests feel normal, collaboration intensifies as teams push toward annual goals, and tool proliferation means employees can't track every service they "might" use.
The common thread: legitimate business processes weaponized through email. Train your team to verify through official channels rather than reflexively clicking, especially when requests come with urgency attached.
Want to explore more? Browse our blog for additional templates, and stay ahead of cyber threats with our curated training resources.
Ready to level up your organization's cybersecurity? Register for a free trial of Wizer Boost to access our full library of phishing templates and exercises!

- Weekly virtual meetups
- Community live streams
- Free resources & more


James Linton, Guest Writer
As a former email prankster turned social engineering and phishing expert, I'm passionate about helping individuals and businesses stay safer in their inboxes. By sharing practical insights on the ingredients of message based deception, and real-world examples of social engineering and phishing attacks, I aim to give fresh perspectives on how to understand the true nature of these problems.
.png?width=501&height=501&name=Phishing-Example-PDFs-sep%20(1).png)