5 Cutting-Edge Phishing Simulations to Master This July
Phishing relentlessly reinvents itself, blending into everyday communication, and 2025 is no different. As new technologies roll out and AI becomes an everyday part of our workflow, attackers are refining their tactics to stay one step ahead. This month’s simulations take advantage of that rapid change, tapping into curiosity, urgency, and the use of new feature packed intelligent apps.
Here are five phishing templates based on current trends and psychological triggers. Each one is designed to test different instincts and help your team spot the kinds of lures that are most likely to slip past their radar.
Download these phishing templates for your in-person security awareness training materials!
Comet's Calling

The Hook: You’ve heard the buzz around Comet Perplexities' new AI-powered browser: it's innovative, exclusive, and everyone wants a piece of it. Then comes the email, an exclusive early access invitation. It taps into the desire for a professional advantage and a limited-time opportunity, all rolled into one. Why wouldn’t you click?
What It Exploits:
Our fear of missing out on new tech, and the desire to be seen as ahead of the curve.
Real-World Risk:
The link leads to a fake login page or triggers a malware download disguised as the browser. From there, attackers could access work accounts or sensitive data.
Learning Moment:
If something promises exclusivity, treat it with caution. Check the offer through official websites or trusted channels, not the email link.
Audit Acknowledgment
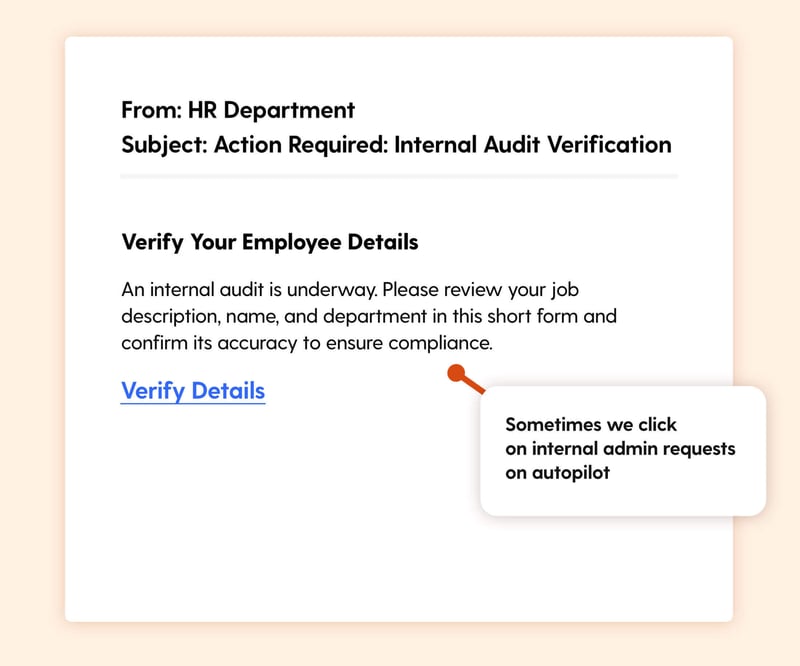
The Hook: An official-looking email from HR or Audit asks you to quickly verify your work details. It’s framed as routine, but the word "audit" adds just enough pressure to make it feel urgent. You don’t want to be the one holding things up, or worse, get flagged.
What It Exploits:
The quiet anxiety about compliance and the ingrained habit of quickly actioning administrative tasks.
Real-World Risk:
The link leads to a fake internal portal designed to steal your login credentials. Attackers could then access employee systems, files, or communications.
Learning Moment:
Even internal requests deserve scrutiny. When in doubt, go to your HR portal directly, don’t rely on email links.
Profile Prospect

The Hook: An alert from LinkedIn says your skills are trending or someone has endorsed you. It's a small dopamine hit: flattering and intriguing. You want to know who noticed you.
What It Exploits:
The natural human desire for professional recognition and the curiosity sparked by unexpected attention.
Real-World Risk:
Clicking opens a fake LinkedIn login page designed to steal your credentials. If compromised, your account could be used to phish colleagues or impersonate you.
Learning Moment:
Social media alerts from LinkedIn are a favorite for scammers to drop into work inboxes. When you get one, go straight to the platform, don’t follow links in emails.
Device Directive
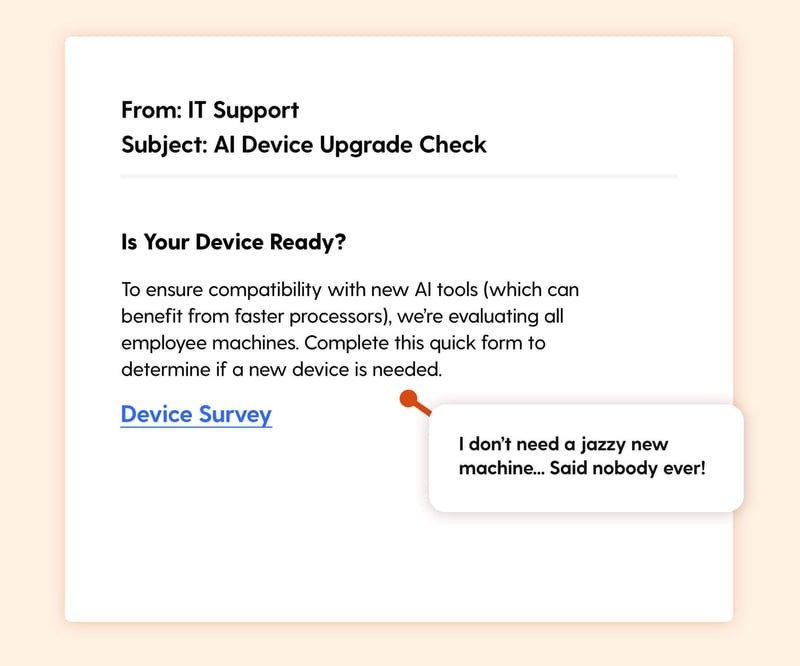
The Hook: An email from IT hints at a possible device upgrade. Just fill out a form, and maybe get a shiny new laptop? It sounds like an easy win.
What It Exploits:
The strong appeal of upgraded technology and the perceived ease of fulfilling a simple, beneficial request.
Real-World Risk:
The link could capture credentials or install malware disguised as a device check. That opens the door to broader system compromise.
Learning Moment:
Upgrades rarely come unannounced. If you’re offered one by email, confirm with IT before acting.
Integration Indication
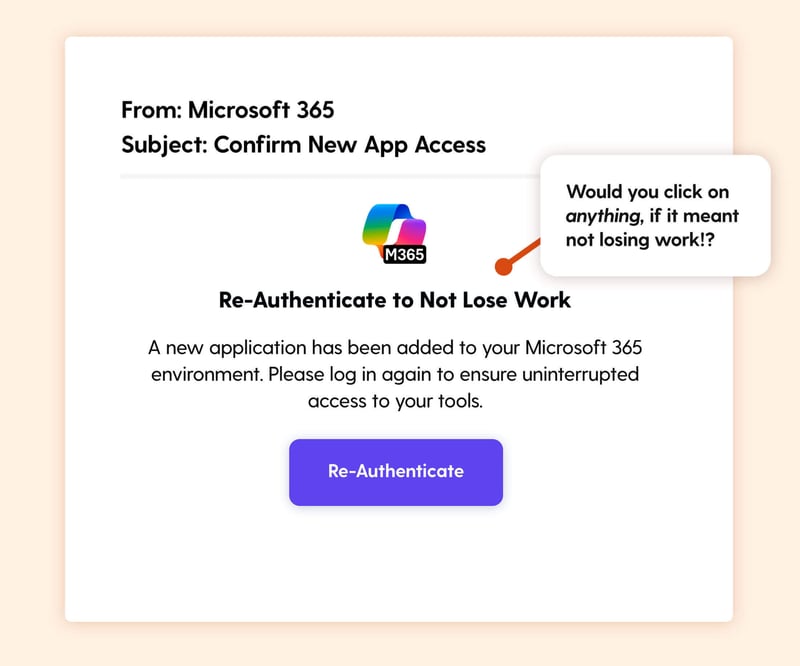
The Hook: An email says a new work app has been integrated, and you need to log in again. It blends seamlessly into the usual stream of software updates, making it feel like just another routine box to tick.
What It Exploits:
The 'autopilot mode' that often kicks in with routine system alerts, encouraging a quick click, login, and move on.
Real-World Risk:
The login page is fake. Once your credentials are entered, attackers could gain access to mail, documents, calendars, the whole suite.
Learning Moment:
Pause before responding to login prompts. If you're unsure, log in through your usual portal and check what's changed.
Build Better Instincts This July
Phishing isn’t about obvious red flags anymore. It’s about blending in. These simulations are designed to help people slow down and notice the moments that don’t feel quite right.
Because the most effective filter isn't the software, it's that quiet voice that says, “This feels off.”
Want to explore more phishing simulations? Browse our blog for additional templates, and stay ahead of cyber threats with our curated training resources.
Ready to level up your organization's cybersecurity? Register for a free trial of Wizer Boost to access our full library of phishing templates and exercises!

- Weekly virtual meetups
- Community live streams
- Free resources & more


James Linton, Guest Writer
As a former email prankster turned social engineering and phishing expert, I'm passionate about helping individuals and businesses stay safer in their inboxes. By sharing practical insights on the ingredients of message based deception, and real-world examples of social engineering and phishing attacks, I aim to give fresh perspectives on how to understand the true nature of these problems.



