What is a Phishing Simulation
The internet is like a minefield of Phishing scams, and they are everywhere - Emails, Text Messages, Social Media, Ads, and even Google Maps. With DeepFake, Voice Cloning, and AI, some are so sneaky that they can fool even the most tech-savvy. This guide will explore phishing in-depth and show you how to spot them.
What is a phishing simulation?
Phishing Simulation means that you will be phishing your own team to test the effectiveness of your phishing training. The simulated phishing emails may look like they are from a manager, vendor, or a well-known brand name. The idea is to find out how good people are at identifying these emails as fake and reporting them. Those who fail the phishing test usually get an explanation of what they can do next time to spot these phishing emails better.
A 1-minute demo of Wizer's Phishing Simulation
Why are phishing simulations important ?
A few reasons phishing simulations tests are important:
- It's an effective way to determine how likely your employees will click on real phishing emails by simulating a phishing attack.
- To ensure people know how to report a phishing attack, for example, by clicking on the “Report Phishing Button” or notifying the Security Team. You don't want people to forward phishing emails to their friends because this may cause even bigger problems. You also want to determine how many people report these phishing emails vs. doing nothing. The more people report the phishing test, the better.
- It's a great way to test the security team's resilience to phishing attacks. What do they do with phishing emails people report? Does the security team follow the playbook? Do they follow up with the people who reported or do nothing?
How does a phishing simulation work?
Phishing simulations are usually done with the help of a phishing simulation solution (like Wizer). There are several components to a phishing campaign:
Phishing Templates
Phishing email templates are usually based on what criminals are using today to attack companies. The idea is that if your team encounters these phishing emails before criminals send them out, they will know to avoid them. Each phishing template usually includes 3 items:
- The Phishing Email Test - This is the email that includes the phishing link that you want people to click or don’t want :)
- The Landing Page - That's the "fake" web page that people will be directed to when they click on the phishing link. Usually, it will look like a Google or Microsoft login page or a page with a link to a file. We typically refer to someone as "phished" if they entered their credentials into these "fake" login pages or downloaded the file. If this weren't a simulated attack, the criminals would now either have the victim's user & password or made the victim download malware.
- The “You Got Phished Page” - We don't steal people's passwords in a simulated attack. Instead, we show them a “You Got Phished” page of what they did wrong. We do this by providing educational material like a video that teaches them how to avoid getting phished next time.
Define Your Target
Next step is choosing your target. Is it the entire organization or a specific department or people? You can use different phishing templates for different groups of users, based on departments, roles, ect.
Reporting
Now that you ran a phishing campaign, it’s time to analyze the results and find out who failed the phishing test. For example, how many opened the emails, clicked, or got phished. Ideally you want those numbers to trend down, however it’s unrealistic that no one will ever click. There is one number that you do want to see trending up. It’s how many people reported the phishing email, because in case of a real phishing attack, you want people to report it. Reporting helps to fine tune your phishing training.
How effective are phishing simulations?
When a phishing simulation is used as a phishing training tool as part of the overall security awareness program, it’s very effective. Part of learning is practicing what you have learned and a phishing simulation does exactly that. It shows people what’s out there and helps them develop phishing spotting skills. However, when used aggressively it can backfire. It could even have a negative impact on the organization’s culture and people may stop responding to legitimate email out of fear.
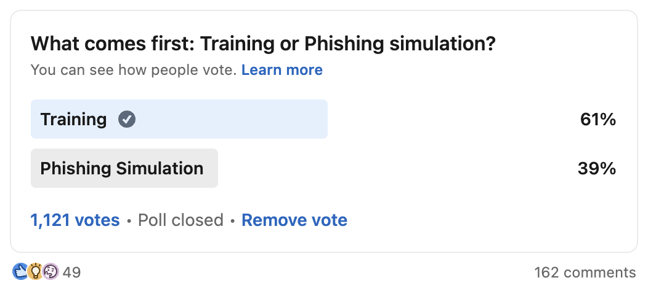
What comes first, training or phishing?
There are two schools of thought here:
Phishing Awareness Training: What’s the point in testing the team if you haven’t educated them?
And
Phishing Simulation - we need to run an initial phishing campaign to create baseline and then measure progress.
So which one is best? We lean more towards Security Awareness Training First and then Phishing Simulation to test the team. Those who prefer to start with Phishing Simulation do this to get a baseline of the current awareness among employees and then run additional phishing tests after people complete the phishing training to check how effective the phishing training was.
We posted this question to the Cyber Security Community and here are the results.
How far is TOO far when running a phishing simulation?
Cyber Criminals have no mercy… But what about us? Should we mimic current phishing scams regardless of how harsh they are because that's what criminals do?
OR
Use phishing templates that are sneaky but won't hurt anyone or negatively impact the organizational culture.
This led to an interesting discussion. You can read the comments here:
There is no straight answer to this question. We posted this question to the security community on LinkedIn, and as you can see, it was almost a 50/50 split.
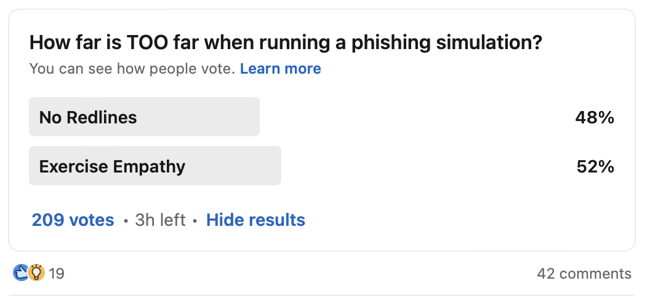
The answer is probably somewhere in between. Just make sure that you involve HR and Legal, because running a phishing campaign can negatively affect the organizational culture and, in some cases, could be illegal.
How often should you phish your employees?
Too much and you end up stressing everybody out, their capacity to think critically will plummet, and you may be literally bullying the workforce by normalizing it. They may become numb to the phishing email and even start ignoring legit emails. Too little, and nobody will learn or retain anything. We suggest running phishing campaigns anywhere between 7 - 12 times a year is a good flow to create good habits and security awareness.
More information about phishing simulation training fro employees you can find here.
What to do with those who fail a phishing simulation?
First you need to define what failure is. Once again, we asked the LinkedIn community and this is what they had to say. The majority think that clicking on a link in the phishing email is enough to fail the test.
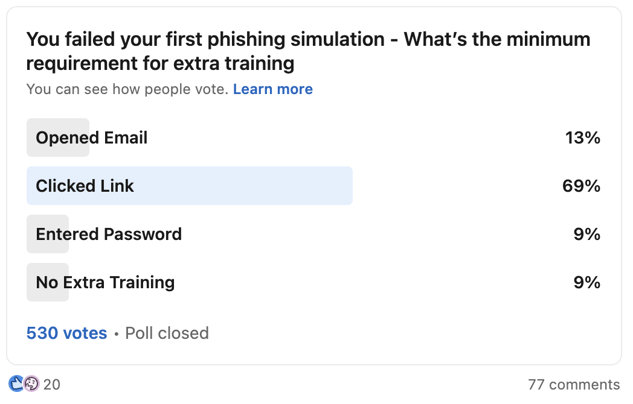
So what do you do with those who fail? People who repeatedly fail phishing tests may endanger the organization; however, they need to be handled with sensitivity, not humiliation. Also, not everyone poses the same threat. If someone with a high level of access like a Senior Manager, someone from Finance, or an IT Admin repeatedly fails a phishing test, it's not the same as someone with a low level of access who fails. How you handle those who fail has to go hand in hand with risk. For some, it may require online 2nd or 3rd tier of remedial phishing awareness training, while others may require in-person phishing training.
In any case, people must know they have an open door and communicate with the security team. Punishing people may backfire, and people may stop collaborating with the security team. However, in some cases, some people may continue to click no matter what, and the organization may not have the expertise to handle psychological aspects. In this case, you may want to limit internet access or change the person's role.
Example of Phishing Simulation Templates
Employee New Time Off Policies
Who doesn't care about Time-Off? The curiosity and sense of urgency makes this phishing email examples very effective.

You Got Hacked
This is a typical phishing email. Someone is trying to hack you and you need to take action immediately to prevent them from taking over your account. Once again the sense of fear and urgency is used to cloud our judgment.
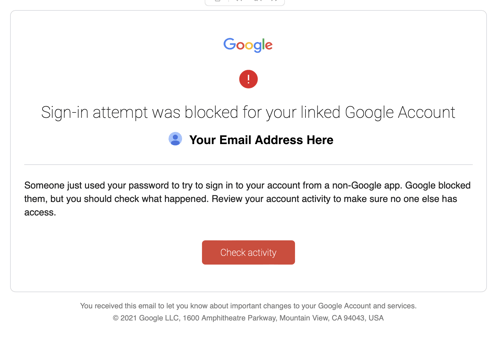
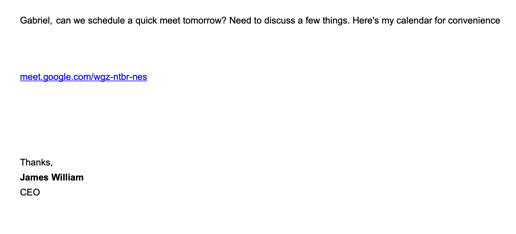
3. The CEO wants to meet
Why does the CEO wants to meet me? This is a spear phishing attack. They know the CEO's name and even the links looks legit, however when you hover over it you will find it's a phishing scam.
What is the most important metric in a phishing simulation?
It depends on your goals. If your goal is to achieve a zero click rate, it’s unrealistic. Some people are going to click no matter what. You cannot rule out car accidents totally, even though everyone has been taught to drive. It is unrealistic to expect that 100% of your people will not click. Even if you get down to a 4% click rate, that may mean 40 people (out of 1000) clicking or 40 open doors for an attacker. Sometimes, numbers can be misleading. If the 4% that clicked include senior managers, people with access to sensitive information, or admin privileges, that may be worse than 10% who have limited access. The most important metric is progress!
Watch our webinar about How to Measure Success.
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.

Gabriel Friedlander
Gabriel Friedlander is the Founder & CEO of Wizer, whose mission is to make basic security awareness a basic life skill for everyone. Wizer has been rapidly growing since being founded in 2019, and now serves 20K+ organizations across 50 countries. Before founding Wizer, Gabriel was the co-founder of ObserveIT (acquired by Proofpoint). With over a decade of experience studying human behavior, he is a prolific content creator on social media, focusing on online safety to elevate public understanding of digital risks. His engaging 1-minute videos have captured the attention of millions worldwide, going viral for their impactful messages.


