Top Cyber Security Quick Guides
Short and simple. Just how we like it. Our Quick Guides are now available in one location. Read the guides from your browser or download them at your convenience.
Guides are always being added so be sure to check back often!
It All Starts With Onboarding…
It’s crucial to instill the importance of security from the very beginning. New hires are often targeted by cyber criminals because they don’t know many co-workers and are more likely to follow direction from someone who pretends to be an executive.
What's in It for Me?
People are more accepting of learning when it’s personal. So, make training personal and teach them how to protect themselves at home, they will soon apply the same behavior at the workplace.
Stay Away From Just Ticking the Compliance Box
If they don't understand the importance of security, they won't take it seriously. And don’t make it a once a year thing, it should be a continuous effort all year long.
Get the Boss (Or Leadership) to Buy-In
Show how security training aligns with organizational goals and specific targets. Remind them that they have a huge target on their back.
How to Convince Your Boss to Invest in Security Awareness
Getting the Employee to Buy-In
Establish a supportive presence by creating a circle of influencers that will act as ambassadors of the training program
Your Ambassador Program
Don't Judge People When They Make Mistakes
Create an open culture where everyone can ask questions without fear. Whenever mistakes happen, use them as teachable moments and not to cast judgement.
Engage and Follow Up
Training is not “set and forget”. Ask employees for feedback and be open to constructive criticism.
Keep it Simple and Real
Don’t assume employees have a technical background, so use simple terms and real life examples they can relate with. And don’t make it childish, adults don’t appreciate content appearing like it was taken from a kids TV show like “Dora the Explorer”.
Face-to-Face is Still a Thing
Training in a classroom is still a thing and very effective. This is usually more expensive, however if you have the budget then don’t rely only on automation, do offline training once a year in addition to your online training.
Make it Easy to Consume
Employees think like consumers, you don’t want them to disengage, so make training frictionless. For example, it should be accessible through their phones with a single click.
Tap Into Existing Resources
Collaborate with HR or the marketing team to create unique content and embed it into existing communication channels. For example, create posters and hang them in the coffee area, write a blog post, or publish a newsletter.
Avoid Surprises
Many people don’t like being surprised at work. So, if you are planning on running a phishing simulation for example, let people know in advance and explain the goal. It may keep them on their toes as they look at every email as suspect.
Get Your Message Across Fast
People are busy, so be short and to the point. Find a balance between continuous awareness training without overwhelming or boring your team.
Mindset
Find a Place and Make it Your Office
Do not share it with others while you are working.
Don't Leave Confidential Information Laying Around
Lock your work device when you are not next to it!
Don't Email Your Printer
Don't email documents to your home printer or to your personal email just to make it easy to print.
Don't Use WhatsApp, Facebook, LinkedIn, or any Other Personal App to Communicate
Only use the tools approved by your organization
Always Call and Verify
Your colleagues are not sitting next to you anymore so call them and verify any request to share confidential data or transfer funds even if they sent it from their email.
Alexa: I'm Listening...
Don't have work sensitive conversations near IOT devices like Siri, Alexa, or Google Home in case they're listening.
Do Not Share Devices or Passwords
Devices are not to be shared with other family members and they must have a unique password and a lock screen timeout.
You are NOT Technical Support
Don't try to resolve technical issues yourself. That could lead to even greater risk. Instead, call your helpdesk.
Don't Let the Browser Remember Your Passwords
If you save passwords to your browser, stop immediately. Use long and complex pass-phrases and don't reuse them.
Technology
Some of the next steps are technical so ask your IT team for assistance. Don't try to do it yourself, that could lead to even greater risk.
Don't Use a Personal Computer for Work
If your company provided you with a dedicated computer or a virtual desktop, use it only for work.
A Wired Network is Better
If possible, connect your work computer to a wired network instead of WiFi.
Using WiFi? Secure It!
If you are using WiFi, it needs to be encrypted using WPA2 or WPA3 and your WiFi name should be hidden.
Separate Your Work Computer From All Other Devices
Create a guest network to separate your work computer from all other devices.
Use a VPN that Your Organization has Provided or Approved
Always Use Multi Factor Authentication to Log In
Use on all Apps, Computers, and Network Devices.
Apply the Latest Security Patches and Enable Automatic Updates
Windows 7/XP? Time to Upgrade!
If you are using an outdated system like Windows 7 or XP, ask your IT team to help you upgrade.
Antivirus, Firewall, Encryption
Make sure you have antivirus installed, your built-in firewall is enabled, and sensitive files are encrypted.
Backup
Consult with your IT team on how and where to back up your data.
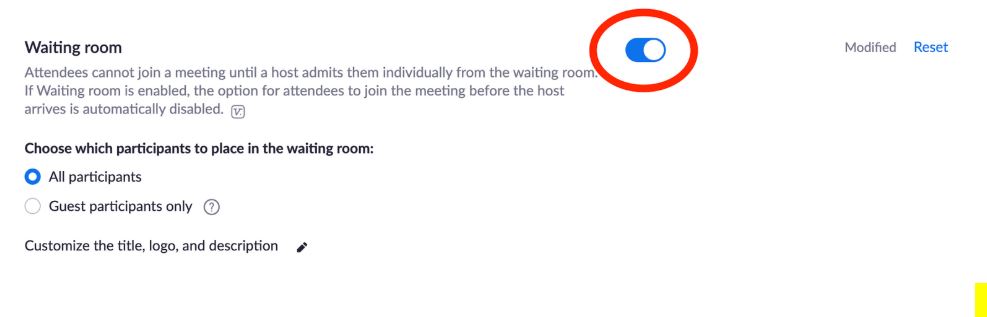
Enable Waiting Rooms
Control who can join the meeting. Users wait in a virtual waiting room until you approve them.
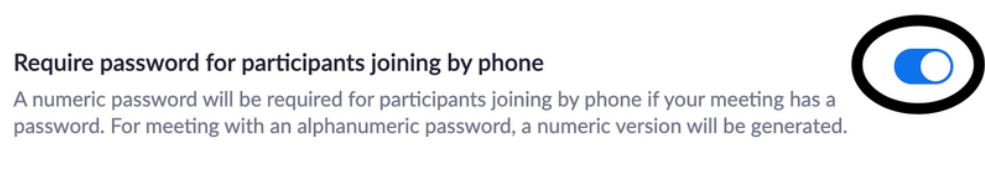
Require a Password When Joining by Phone
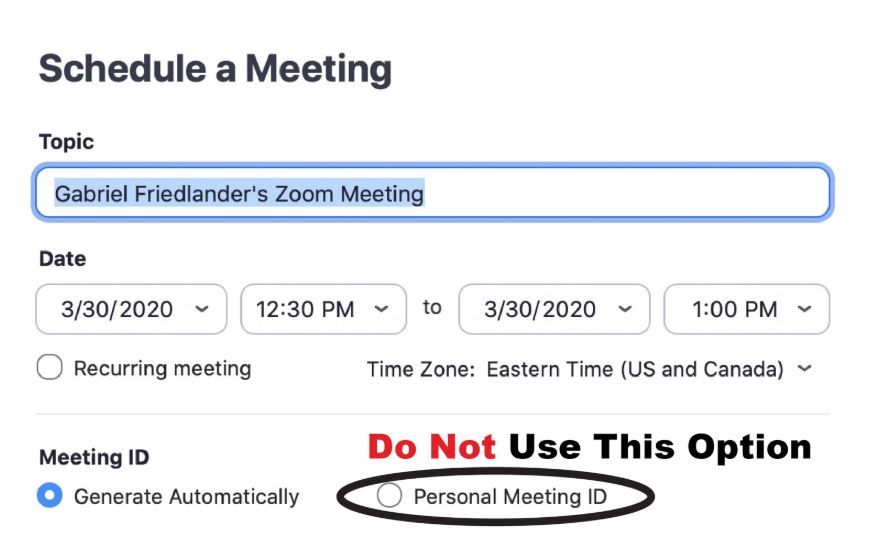
Do Not Use a Personal Meeting ID
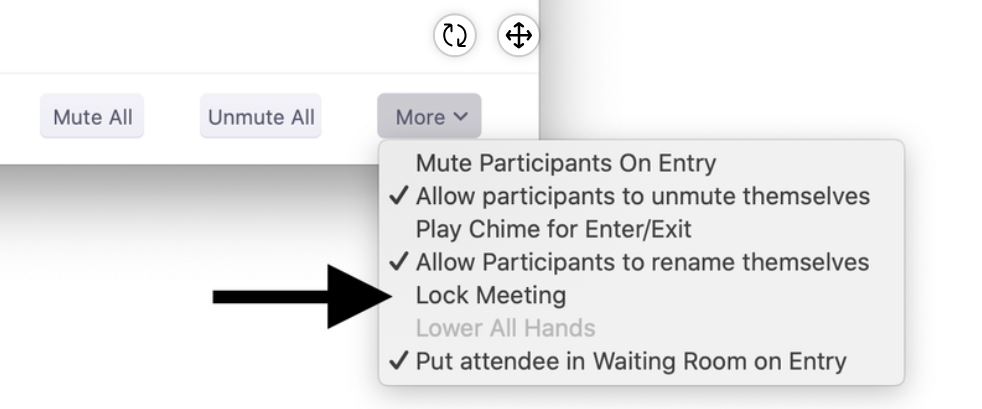
Lock the Meeting When Everybody is in
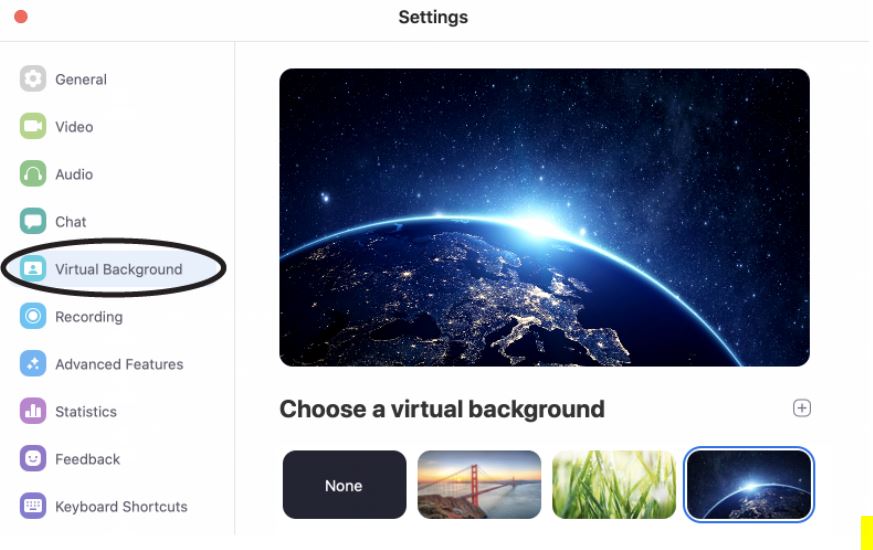
Enable Virtual Background
A Few More Recommendations
- Always require a password
- Disable file transfer
- Mute participants upon entry
- Screen sharing - host only
- Require a password for Personal Meeting ID (PMI)
Change the Default Pin Code
Keep Smart Devices on a Separate WiFi Network
Disable Streaming Services You are Not Using
Make Sure All Your Devices are Updated Regularly
If automatic updates are available for software, hardware, and operating systems, turn them on.
Don't Reuse the Same Password on all Devices
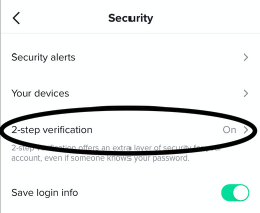
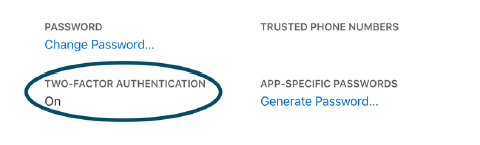
Turn On Two-Factor Authentication
Don't Place Smart Devices with Cameras in Bedrooms
Do Not Sign Up for Free Premium Accounts, Game Tokens, Skins, or Weapons
This is phishing! Hackers will capture your password, steal the account, or your identity.
Beware of Fake Social Media Accounts
Hackers can create fake social media accounts with the same name and thumbnail of your favorite YouTuber...If It Sounds Too Good to be True, Then it Probably Is
Hackers often use ads that promote huge discounts. These are scams.Enable Multi-Factor Authentication Wherever Possible
This prevents hackers from accessing your account remotely even if they know your password.Do Not Reuse the Same Password for All Accounts
If you're using the same password for different websites, then all of your accounts are at risk.Use Strong Passwords
Use a phrase as your password, the longer, the better.Sexting is Illegal Including Sending or Keeping Pictures
These nude photos are considered child pornography, whether they include a face or not!What? Who is This?
So, You are Saying it is Urgent...
If it is Too Good Too be True, Then it Probably is!
Yes, We Accept Gift Cards
6 Common Scams
1. Warning! Your Computer is Infected.
2. Billy, Is That You?
3. Look Out For Your New Medicare Card!
4. The Miracle Cure!
5. Congratulations! You Are a Winner!
6. Knock, Knock! Who's There?
Before We Start, Here Is What People Are Saying...
- I bought Nike trainers and they never arrived...
- I bought a shed for $139 and never received it. It was a scam on Facebook...
- I was scammed twice. Unfortunately, I bought on the same day, a flashlight and weights. PayPal sucks, no help...
- I was suckered twice. No more!! I will never buy anything off a Facebook ad again, ever!
- I also fell for two FB ad scams. One was for a small belt sander for $39.95.
- Facebook is driving me nuts with all the scam duplicate selling sites.
Top 10 Tips to Avoid Scams
1 .Don't blindly trust slick video content or pictures, many are simply taken from the original sites.
2. If the advertised price looks too good to be true, it probably is.
3. Don't buy from Facebook pages or websites you've never heard of before. That's like buying from a random person on the street.
4. Google the exact wording in the ad. Many scams can be found this way.
5. Google the product or the website name along with the phrase "scam."
6. Don't trust an ad just because it appears on a reputable site. Scammers post fake ads everywhere!
7. If you are constantly served the same ad, and the price is dropping, it's probably a scam.
8. If most of the reviews are within several days, then they are probably fake.
9. Look out for domains with extensions like ".site" or ".shop." Scammers prefer them because they are cheaper than ".com."
10. Watch out for ads that show popular products from crowdfunding sites such as Kickstarter, it's a common scam.
It's Not Instead Of...
Cyber Insurance is the last resort if all your other defenses fail you.What Will They Pay For?
The provider will pay for data breach recovery including business interruption costs, data loss, your reputation, and much more.Anything Else?
A good provider will include pre and post breach services like risk assessments, penetration testing, monitoring, employee security awareness training, forensic services following a breach, and much more.So How Do You Find a Good Insurance Company?
- Look at how many claims they have paid out.
- Talk to friends and colleagues and find a broker.
- Review their before and after breach services.
- The details of the coverage and policy should be easy to read.
- Cyber Insurance should always be purchased as a standalone service and within your own country.
Backups are Extremely Important and are a Must Have
This is especially important in the case an attacker uses malware to lock you out of your computers.Limit Access to the Internet as Much as Possible
For example, do not allow employees to browse the web from your POS terminal.Educate Your Employees About Cyber Threats
If employees are not trained, then the risk they will get infected increases dramatically.Lock Down Your Computers
Make sure employees have limited permission. For example, they should not have permissions to install apps.Get a Firewall and Configure it Properly
This will limit who can access your business from the outside and will control how data exits your business.Know What Apps and Computers are Installed and Ensure They are Updated and Patched
Unpatched computers and apps are open doors for cyber criminals.Set Up Complex Password Policies
Make sure employees use complex passwords and do not access computers with admin accounts or share passwords.Have Clear Termination Policies
Make sure terminated employees don't have access to business systems and emails anymore.Check for Vulnerabilities That May Allow Attackers In
Attackers are also using vulnerability scanning on your network to try to get in, so you better be ahead of them.Install Antivirus on All Computers and Devices
This will stop known viruses from infecting your network.Set Up an Email Security Gateway
This will check incoming emails for viruses, malware, spam, and other types of attacks before the email arrives to your inbox.Set Up a Virtual Private Network (VPN)
This will ensure that if anyone connects to your network, they will not be able to see the data you are sending over the network.Don't Do It Yourself
- Hire someone.
- Not every business is the same, so identify any risks that can cause harm to your business.
- Have a plan for what to do if your business does get hacked.
Don't Take a Selfie With Your Badge Showing and Post it on Instagram
Cyber Criminals can clone your badge, change the photo, and pretend to be you.Don't Post a Video Blog of a Day at the Company
That's like allowing criminals inside the company walls. The office space is full of confidential information.Don't Share Your Password With Anyone
Even with the IT Department. Only you should know your password.No One Will Ask You to Buy Gift Cards
That's a common scam. There is no special celebration that requires you to secretly get gift cards for everyone...Be Aware of Scam Emails
Because you still don't know many people, you are more likely to follow direction from someone who pretends to be an executive.If it's too good to be true, it probably is.
Be aware of unrealistic discounts or coupons, many of them are scams.Avoid buying from sites you don't know.
Purchasing from known sites reduces the risk of being scammed.Don't scan QR Codes.
Criminals can place their own sticker over the legitimate one so that whenyou scan it, you will be redirected to a fake site.
Don't use free WiFi to check prices.
Criminals can connect to your device. Instead, use mobile data or a VPNVerify You're on the Correct Shopping Cart Page.
You may be on a fake page that looks like the official one.
Pay With a Credit Card.
You may be paid back if you quickly report fraudulent transactions. Don't use a debit card.
Even Better...Pay With a Gift Card
Gift cards are not tied to your bank account and have a limited amount.
Only Use Websites That Start With "HTTPS:"
Ensure the "s" is in there and there is a lock next to the URL.
Watch Out for Emails About Shipping Issues.
Don't click on any links. Instead, manually go to the official site and check if there are any issues.
Avoid Posting Online What You Purchased.
Scammers may try to follow up with you pretending to be the merchant.
Not Sure About a Site or Link?
Run the URL through VirusTotal.com to check if it's fine.
Received a Gift Card? Make Sure It's Legit.
If someone sent you a gift card, thank the person who gave it to you to make sure it is legit BEFORE you click on it!
Don't Accept Electronic Gifts Such As USB Memory Sticks.
They can be full of malware.
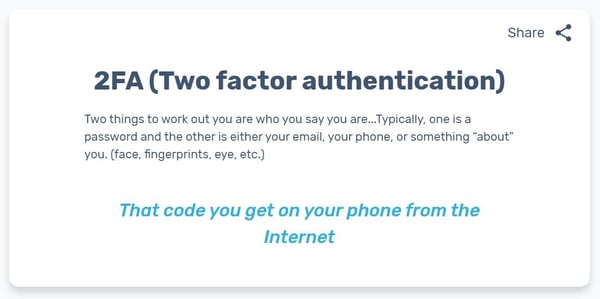
1. Google
https://myaccount.google.com/security
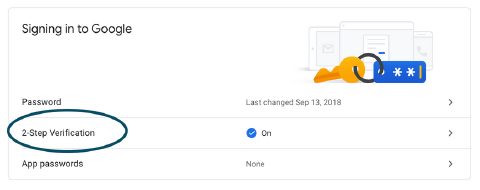
2. Facebook
https://www.facebook.com/settings?tab=security
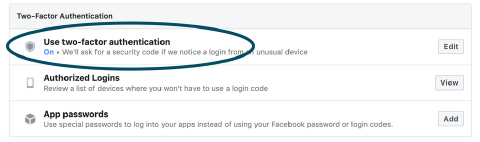
3. Instagram
Settings > Security > Two-Factor Authentication
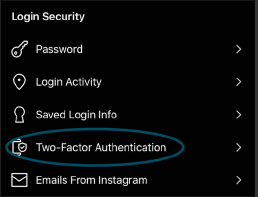
4. WhatsApp
Settings > Account > Two-Factor Authentication
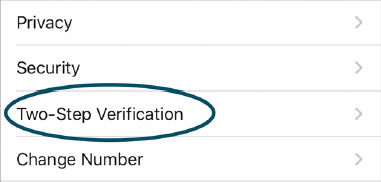
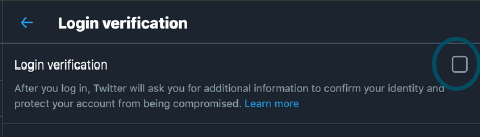
5. Twitter
https://twitter.com/settings/...
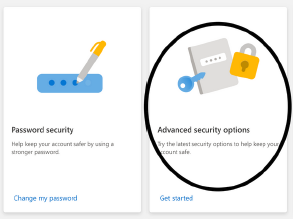
7. Microsoft
https://account.microsoft.com/security/
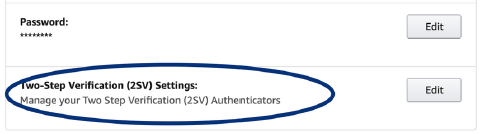
8. Amazon
Your Account > Login & Security
9. LinkedIn
https://www.linkedin.com/psettings/...
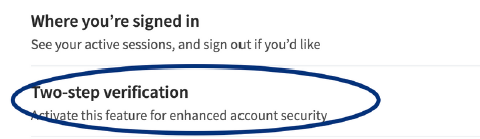
10. Reddit
https://www.reddit.com/settings/privacy
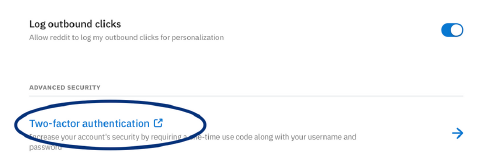
11. TikTok
Settings -> Security